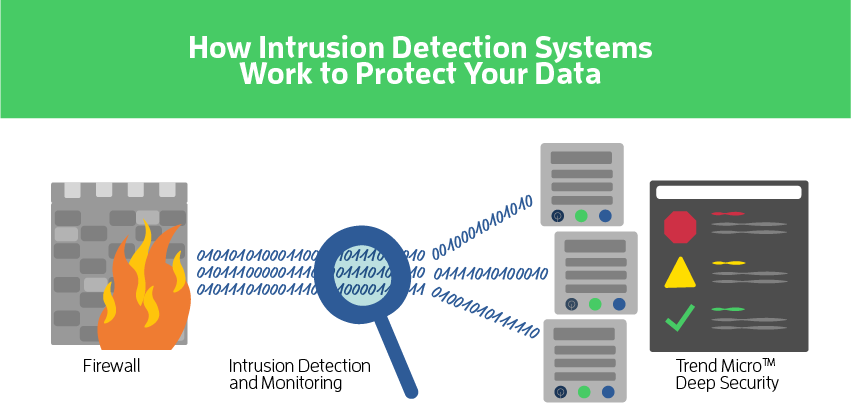
Should you invest in an Intrusion Detection System? Responsible businesses with sensitive data know they need a firewall to control traffic and secure their networks. What seems less well known, however, is the role that complementary technologies play in a comprehensive approach to cybersecurity. An Intrusion Detection System (IDS) enables organizations to take a proactive security stance, which is why Atlantic.Net offers one for its security-conscious customers.
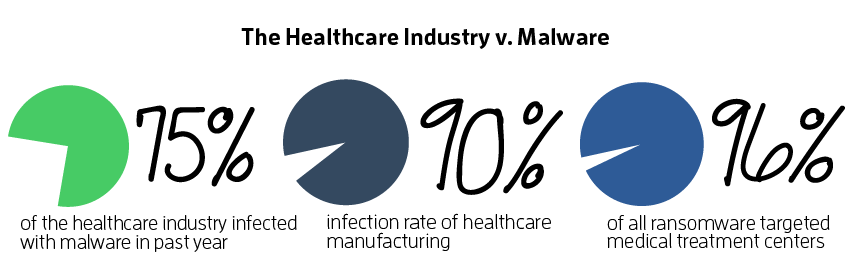
Amid all the headline-grabbing data breaches of the past year, the vulnerability of companies in industries like health care may be overlooked. Data breaches began costing healthcare firms over $5.5 billion annually shortly after HIPAA became law, according to the Ponemon Institute.
Cliches like the typical hacker being a teenager living in his or her parent’s basement are persistent, and harmful because they misrepresent the situation to the potential victims of hacking. The numbers clearly show that hacking is now predominantly committed by sophisticated criminal organizations. Utilizing an IDS is a proactive approach to meeting that threat.
An Intrusion Detection System, or IDS, is a software application that monitors the network and hosting environment and analyzes activity on it. Any activity which is considered unusual is ranked according to how high risk it is considered based on information from global threat databases.
How Intrusion Detection Systems (IDS) Protect You
Once deployed, the IDS analyzes the patterns of network traffic and compares critical files to previous versions to identify any possible changes. It does this with deep analysis of the packets that make up network traffic, whereas the firewall examines the packet “headers” or labels to screen out those which it knows do not belong.
That judgment is based on comparisons with known attacks, gathered from threat databases, to normal activity. This analysis allows security teams an opportunity to identify and respond to attacks, even if they are cleverly disguised in completely new ways before the attack has been completed and the damage was done.
An IDS is typically either a network or host-based system, or a hybrid of the two.
IDS provides a constantly updated list of the potential issues with a network. This gives the organization an opportunity to identify risks which must be investigated or dealt with and creates records that indicate the diligence of the company using it. It can help with attack prevention, preparation, and response time, which is critical for mitigating cost and damage. It can also help with visibility, which enables the IT or security team to manage the network more efficiently. Together these benefits can play a critical role in ensuring regulatory compliance.
A more holistic approach, including passive technologies like a firewall, as well as active monitoring, endpoint detection, and vulnerability management, is gaining acceptance as the best practice for security. A survey of IT professionals released in May by IT management company SolarWinds found that among those who said their companies are less vulnerable than a year ago, adoption of IDS and related tools was the top reason why.
Atlantic.Net’s Comprehensive IDS
To protect clients at both the network and host level, Atlantic.Net provides a dual IDS solution, which works with your firewall, inspecting packets the firewall accepts as appearing to be legitimate.
The Atlantic.Net proprietary IDS is custom-built from industry-leading open source technology. It resides on the network, protecting against local vulnerabilities on the hardware side. As an open source-based solution, the Atlantic.Net proprietary IDS can utilize the community’s consensus rule base, and then customize it to fit the specific needs of the computing environment it protects.
The host-based Trend Micro Deep Security IDS is provided by Atlantic.Net to protect critical infrastructure against network vulnerabilities from the server side, whether those servers are dedicated, virtual, or cloud.
Trend Micro Deep Security includes protection against malware, including ransomware, targeted attacks, and advanced threats.
The two are managed with a unified interface, so Atlantic.Net can review the incident logs they generate and alert the client when threats are suspected or action is needed. Thousands of reports can be generated on a busy public network in a very short amount of time, so the ability of the IDS to rank incidents, and of the host to manage the reports, is crucial to getting the full protection of the technology for the best possible value.
The technologies are quickly and easily integrated into your network environment, and after incorporating it into your environment, you can choose to receive regular weekly or monthly reports summarizing current vulnerabilities. These reports help those in regulated industries and are in addition to any critical alerts which the Atlantic.Net IDS discovers.
A complete and proactive security stance is necessary for every organization with valuable information and systems to protect against a constantly shifting and evolving threat landscape. For companies with sensitive data subject to regulatory compliance regimes, an intrusion detection system can be an invaluable part of that responsible corporate stance. It can be taken for granted that a reputation-destroying data breach will make headlines before too long. With Atlantic.Net’s comprehensive IDS solution, you can help avoid your company’s sensitive data falling into the wrong hands.
Contact [email protected] for more information on our HIPAA-Compliant, Dedicated and Cloud IDS solutions today!
Read More About Intrusion Prevention
- Intrusion Prevention Systems from Atlantic.Net
- What Is an Intrusion Prevention System?
- Penetration Testing Best Practices
Trend Micro and Deep Security are registered trademarks of Trend Micro Incorporated.