
GPU for Data Science: 4 Free Libraries and 6 Best Practices
January 4, 2025 by Gilad Maayan
What Is GPU Acceleration in Data Science? GPU […]

GPU Virtualization: Techniques, Solutions, and Best Practices
January 3, 2025 by Gilad Maayan
What Is GPU Virtualization? GPU virtualization allows multiple […]

GPU for Rendering: How It Works, Top 10 GPUs and Pro Tips
January 2, 2025 by Gilad Maayan
How Are GPUs Used for Rendering? A graphics […]

How Virtual GPUs Work, Use Cases and Critical Best Practices
January 1, 2025 by Gilad Maayan
What Is a Virtual GPU? A virtual GPU […]

NVIDIA NVLink: How It Works, Use Cases, and Critical Best Practices
December 31, 2024 by Gilad Maayan
What Is NVIDIA NVLink? NVLink is a high-speed […]

What Is VPS: 2025 Buyer’s Guide and Expert Tips
October 30, 2024 by Gilad Maayan
What Is a VPS? A virtual private server […]

API Security in a HIPAA Compliant Environment
October 29, 2024 by Gilad Maayan
What Is API Security? API security is the […]

VMware vs. Nutanix: Which Is Preferred in HIPAA Compliant Environments?
October 28, 2024 by Gilad Maayan
What Is VMware? VMware is a provider of […]
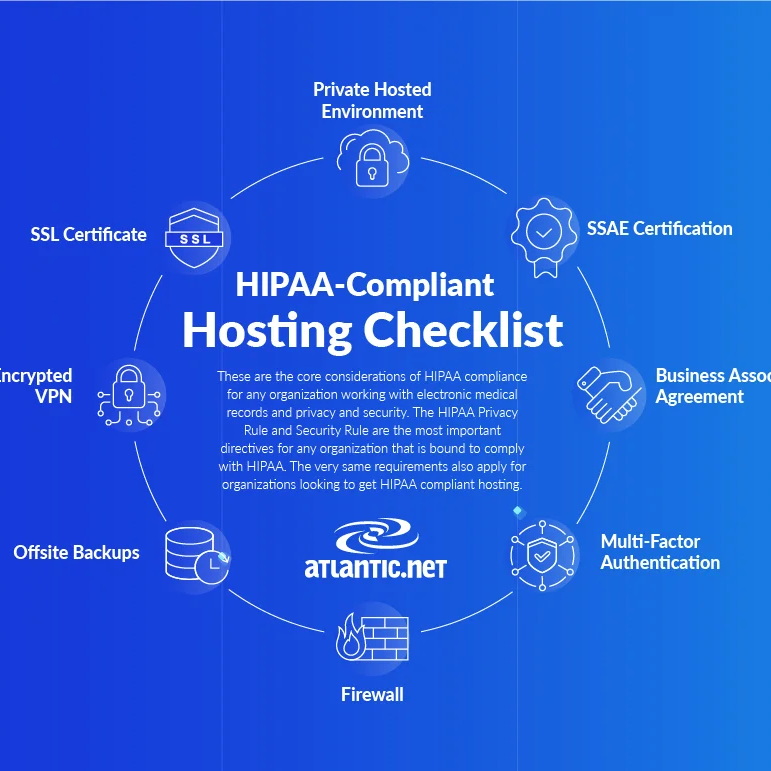
What Is HIPAA Compliance? History, Rules, and Requirements
October 3, 2024 by Gilad Maayan
What Is HIPAA Compliance? HIPAA compliance refers to […]

What Is PCI Compliance? 12 Requirements, PCI Levels, and Penalties
September 30, 2024 by Gilad Maayan
What Is PCI Compliance? The Payment Card Industry […]

VPS Hosting vs. Shared Hosting: Pros/Cons, Differences, and Expert Tips
September 26, 2024 by Gilad Maayan
What Is VPS Hosting? VPS (virtual private server) […]

The 4 Levels of PCI Compliance: What You Need to Comply
September 25, 2024 by Gilad Maayan
What Are PCI Compliance Levels? PCI (Payment Card […]

What Is Dedicated Server Hosting?
September 24, 2024 by Gilad Maayan
What Is Dedicated Server Hosting? Dedicated server hosting […]

Using AI Coding Assistants in a HIPAA-Compliant Environment
August 30, 2024 by Gilad Maayan
What Are AI Coding Assistants? AI coding assistants […]

What Is a Bare Metal Server? Benefits, Use Cases, and Best Practices
June 3, 2024 by Gilad Maayan
A bare metal server is a physical server […]

Bare Metal Kubernetes: Pros, Cons, and Best Practices
June 2, 2024 by Gilad Maayan
What Is Bare Metal? Bare metal refers to […]

Kubernetes In a HIPAA Compliant Environment: Key Considerations
May 2, 2024 by Gilad Maayan
What Is Kubernetes and How Is It Used […]

HIPAA Compliant Software Development: Principles and Best Practices
April 12, 2024 by Gilad Maayan
What Is HIPAA Compliance? HIPAA, the Health Insurance […]

Application Security Requirements in the HIPAA Framework
March 28, 2024 by Gilad Maayan
What Is the HIPAA Framework? The Health Insurance […]

How to Ensure Payment Security for Your eCommerce Store
February 27, 2024 by Gilad Maayan
Payment security protects potentially the most important sensitive […]