A proven and reliable cybersecurity strategy is a major driving force behind business decision-making within the modern global organization. Having the ability to protect and secure information technology services enables tech-savvy organizations to prove that they can control and secure the network. Securing business assets is essential to help prevent information exposure or data breaches of confidential business data.
Monitoring and Preventing Unwanted Traffic That Poses Threats to Your Organization
Most industry professionals already know how to protect their infrastructure with network firewalls and a securely architected networking design. A more recent technology, known as an intrusion prevention system, is a software image or hardware-based appliance for the security-conscious organization. It monitors the entire network and hosting environment by analyzing traffic and network activity throughout a corporate network. An IPS application is sometimes referred to as a security information event management (SIEM) system.
A typical setup includes IPS appliances at various layers of the network, usually at choke points on the perimeter network. Each network packet is monitored and ranked according to a risk policy based upon information concatenated from a vast number of global threat prevention databases. The global database is used to compare networking data packets with known exploits or vulnerability hashes. This approach enables businesses to be on the forefront of the latest global threat trends and risks within the cybersecurity industry.
An IPS solution is designed to monitor and alert against scenarios such as an application or operating system exploit, buffer overflow attacks, unauthorized port scanning, cross-site scripting exploits, and many other vulnerabilities.
How does an Intrusion Prevention System (IPS) work?
The first time an IPS is configured and deployed within a networking environment, the IPS will securely scan the network and create a baseline of the current usage scenario of the compute, storage and networking configuration. Over time, the IPS will analyze all network traffic and start to compare changes against the baseline configuration. This enables the IPS to generate an anomaly-based identification intelligence that can work out what traffic is considered a threat.
TCP/IP network packets are multiple data objects that traverse the network at a single time. Each packet contains information such as a source and destination IP address, the data itself, information regarding QoS, and how the packet should be handled. All this information is encapsulated within the packet prior to being transported over the network.
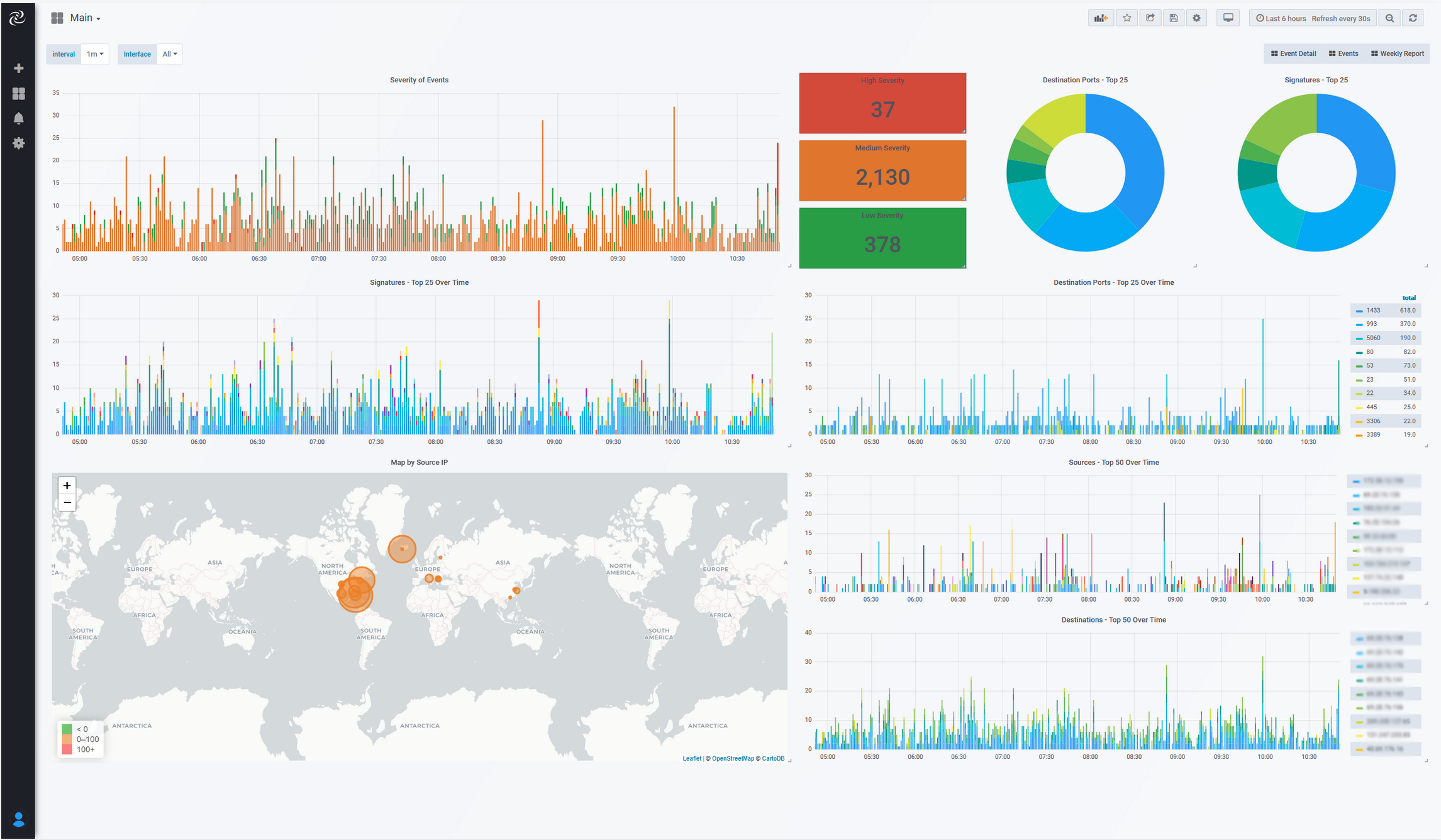
The IPS screens each packet, which can help detect intrusions. This is done by comparing intercepted local data packets with information known about previous attacks via the global threat databases. This intelligence can be configured to trigger alerts and automatically raise incident reports which will allow a dedicated security team to identify and respond to suspicious traffic before any damage is done to the infrastructure.
The IPS will look for a signature-based flow of traffic that perfectly matches the previously known attack signatures over the network, and it will result in an ALLOW or DENY to the network request.
This intelligence is vital to help provide an organization with the opportunity to identify threats and risks. It can help with attack prevention, preparation, and response times by identifying behavior-based network changes. An IPS can also help with infrastructure visibility which enable engineers to manage a network more efficiently by monitoring and blocking unexpected network traffic, such as network traffic over higher port ranges or file transfers at unexpected times of day or night.
The Atlantic.Net Comprehensive Intrusion Prevention System (IPS)
To protect our valued clients at both a networking and hosting level, Atlantic.Net provides a dual IPS solution that implements a NIPS (Network Intrusion Prevention System) and HIPS (Host Intrusion Prevention System) solution.
The IPS is placed at strategic points within a network and works with your firewall by inspecting packets that the firewall has already accepted as legitimate. Another IPS resides directly on the network, protecting against local vulnerabilities on the network layer.
The first part of our IPS solution is a custom-build NIPS platform created by our experts using industry-leading, open-source technology. As it is based on open-source technology, the Atlantic.Net proprietary NIPS appliance can utilize a community consensus rule database and then customize it to fit the specific needs of the computing environment it protects.
Secondly, Atlantic.Net provides the host-based Trend Micro Deep Security HIPS to protect critical infrastructure against network vulnerabilities from the server-side, whether those servers are dedicated, virtual, or cloud. Trend Micro Deep Security includes protection against malware, including ransomware, targeted attacks, and advanced threats such as logging privileged user account access.
Both technologies are managed within a unified dashboard interface, allowing Atlantic.Net the ability to review the incident logs that are generated and automatically alert when a threat is identified or suspected. These detailed information logs can be extensive and can add up significantly within a short space of time, so the ability to rank and classify each identified incident is a priceless feature when attempting to get an accurate overview of what is happening on the networking estate.
With this, we offer excellent reporting facilities built into the IPS solution; the reports can be as granular or as high-level as required. Users can choose to receive weekly or monthly reports summarizing the current infrastructure vulnerabilities. These reports provide invaluable insight and are a perfect match for clients in regulated industries. The reports are offered in addition to any critical alerts which the Atlantic.Net IPS discovers.
To keep your network safe from attackers, Atlantic.Net uses Cisco-developed packet analyzer software that scans your network traffic for malicious activity. As an open-source network intrusion prevention system, this software can perform real-time traffic analysis, packet logging on IP networks, protocol analysis, and content searching/matching, and can also be used to detect a variety of attacks.
Next Steps
When you choose to work with Atlantic.Net, you can rest assured that your system will be protected with state-of-the-art IPS software. Our team can install and configure the software on your behalf and monitor your network for operating system fingerprinting attempts, common gateway interface, buffer overflows, server message block probes, and stealth port scans. You will not have to be concerned about updates and reporting. While business is free to innovate, Atlantic.Net will ensure your systems are running safely and smoothly. Get started with an IPS from Atlantic.Net today.
Read More About Intrusion Prevention
- Intrusion Prevention Systems from Atlantic.Net
- Intrusion Detection Systems from Atlantic.Net
- Penetration Testing Best Practices