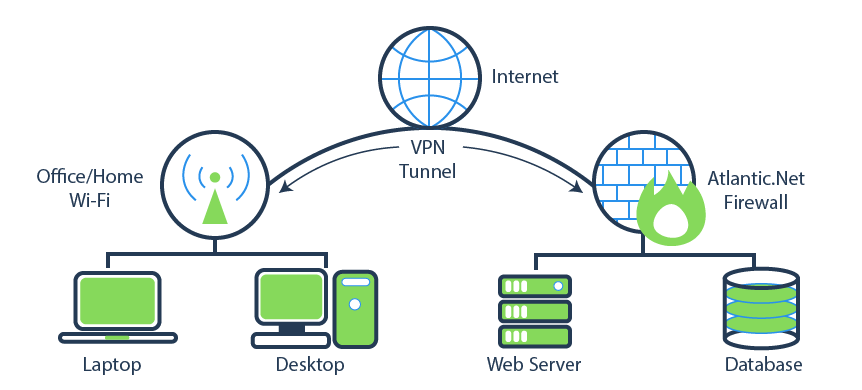
As we continue to rely more on technology, keeping our information safe is becoming increasingly difficult. With Wi-Fi being the standard form of network communication for most business professionals who are on the go, the need for secure data transmission has become even greater. Public Wi-Fi locations like coffee shops, the airport, and even your home and office are not safe when sending and receiving data. According to idtheftcenter.org[i], in 2015 alone there were over 177 million cases of identity theft reported.
How do hackers access my data?
The two most popular ways of someone accessing your data over Wi-Fi are sniffing and rogue access points[ii].) Sniffing is when another user nearby captures the data your computer transmits over Wi-Fi, and then reassembles it to look for passwords or other unencrypted account information. The aptly named rogue access point is where someone will create a Wi-Fi hotspot that appears to be legitimate, like “Free Starbucks Wi-Fi,” or “Airport Public Wi-Fi,” and then waits for users to connect to it. Once the user is attached to the hacker’s hotspot, the users’ data transmission is all captured on the hacker’s machine. The hacker can then use specialized programs to reassemble the packet capture to reveal what the user(s) was looking at and if any sensitive information or passwords were used. One of the most effective solutions is to encrypt the traffic going between your infrastructure and your home computer/laptop, which is why VPNs were developed.
What is a VPN?
First developed back in the early 90’s, a VPN, or virtual private network, is a means of allowing a computer over a public network to access a remote private network[iii]. A VPN allows your computer to communicate with an external private network as if it were connected locally. This is especially important for large organizations and governments that have users connecting over public networks. Before VPN technology, the only way to achieve this was to run a direct link between the two locations. While a VPN by itself makes transmission easier and integrates easily into existing internet infrastructure, a VPN alone provides no form of secure communication.
Secure VPNs protocols were developed to help solve this problem. By creating an end-to-end encrypted connection, or tunnel, between a device (or router) and the remote private network, only computers and networks that have the unique key can decode the data. Data sent out from each end of a VPN encrypts packets with one of two types of encryption: symmetric-key or public-key. With symmetric-key, packets are both encrypted and decrypted with the same key. In public-key, the data sent over the network is encrypted with a public key, while a private key is stored on each computer to decrypt the data[iv].
HTTPS
One type of VPN that you use without even noticing it happens right in your browser. Short for Secure Sockets Layer, SSLs are a form of virtual private networking. Every time you access data from a site that transfers over SSL (HTTPS) with a valid certificate, your internet browser is encrypting your data before sending it to the website. This encryption happens seamlessly in the background, so it is easy to forget how important this technology can be, especially for businesses that can be fined for not securing sensitive data during transmission, like the medical and financial industries.
For all other forms of data transmission between you and your servers, Atlantic.Net recommends IPSec or OpenVPN.
IPSec
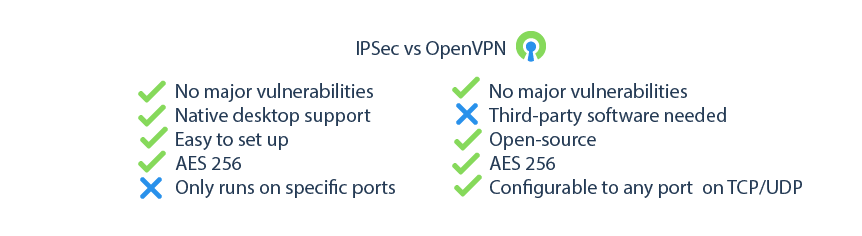
IPSec, or Internet Protocol Security, is natively supported on most desktops, mobile devices, and routers. IPSec supports two ways of connecting clients: via a tunnel or by a mobile connection. An IPSec tunnel is typically set up between two private networks via their routers. This can reduce the time it takes to set up users being able to access the VPN since the individual computers do not require setup. IPSec mobile allows a single user to connect with a login, password, and preshared key. This is ideal for users who are connecting while out of the office. The downside to IPSec is that it only transmits on specific ports, meaning it can be easily blocked.
OpenVPN
OpenVPN, as its name indicates, is an open-source VPN technology. It is highly configurable, very reliable, and incorporates OpenSSL encryption. Unlike IPSec, OpenVPN is more difficult to block, as the port it communicates on can be changed to any port. It is not without its downsides, though. OpenVPN is more tedious for a beginner to set up, as it has a lot more ways to customize the VPN. Most desktop operating systems do not natively support it yet either, which means you will need to install a third-party client. At Atlantic.Net, we have found that OpenVPN benefits many of our customers who more fine-grained control over access, as it allows individual user logins to be assigned a static IP address on the VPN. This then allows per-user access restrictions through an Atlantic.Net Firewall.
Atlantic.Net VPN
VPNs are secure, accepted, and cost-effective alternatives to connecting to your data remotely. No matter which VPN solution you choose, Atlantic.Net has the expertise and infrastructure to help you protect your data. We offer a range of solutions, ranging from SSL certificates for your website to VPN tunnel and client connections. Our Atlantic.Net firewall solutions are available for both our HIPAA Cloud Hosting, HIPAA-Compliant Website Hosting and Dedicated customers and come with VPN included. Contact [email protected] today for more information!
By Justin VanSyoc and Derek Wiedenhoeft
[i] ITRC Breach Stats Report Summary 2015 pdf