The healthcare industry has been a primary target of data hackers for several years. There are numerous reasons for this. First, the healthcare industry offers a lot of valuable information to successful hackers – social security numbers, names, addresses, Medicaid ID numbers, medical records, health insurance information, and more – can all be scraped from a successful breach. It’s a literal goldmine for hackers.
Healthcare as a Cyberattack Target
The cyber attackers tend to target hospitals, pharmacies, health insurance companies, urgent care clinics, and other healthcare industry targets, not just for the wealth of information to be stolen, but for another very simple fact: the healthcare industry has long been regarded as having weak cybersecurity overall. In fact, here are some statistics from a SecurityScorecard report:
- 88% of all healthcare manufacturers have been infected with malware at some point.
- Medical treatment centers account for 96% of ransomware targeting the healthcare industry.
- More than 50% of the healthcare industry scores lower than a C grade in network security.
- The healthcare industry ranks 15th for susceptibility to social engineering tactics.
- 63% of the 27 biggest hospitals in the U.S. have poor ability to implement software security patches on time.
- Healthcare ranks 9th overall in security rating compared to all other industries.
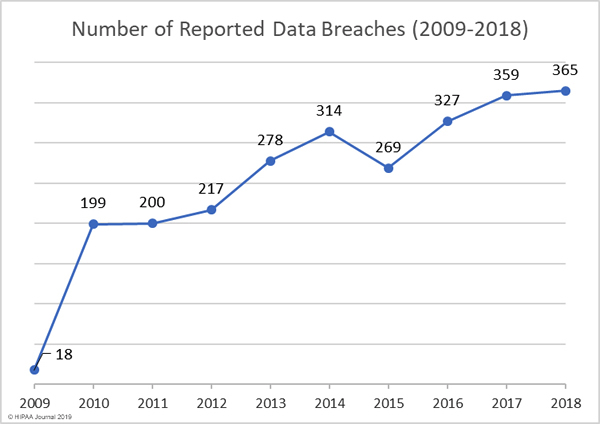
So in a nutshell, the healthcare industry is a low-hanging fruit that offers sweet, ripe rewards to hackers. More cyber-attackers have realized this in recent times, leading to a serious spike in attacks on the healthcare industry since 2009 until now.
Protecting Your Medical Data from Hackers
Consumers have very little recourse. LegalZoom, a company that offers legal forms and legal advice, suggests the following measures to protect your medical record privacy:
- When asked to sign a release, try to limit the amount of information divulged by crossing out the boilerplate language and filling in more exacting terms.
- Discuss your confidentiality concerns with your doctor.
- Ask your health care provider to not photocopy more records than necessary.
- Ask about your health care provider’s policy on the use of wireless communication and fax machines.
- Be aware that marketing-related questionnaires and health screening at malls and other public places may gather and distribute your medical information.
Healthcare Industry Data Breach Statistics:
There has been a huge upward trend in the number of records exposed per year, with 2015 being the worst. More than 113.27 million records were exposed by data breaches in 2015. Fortunately, that amount dropped significantly back down to normal levels for now, but 2015 should definitely have been a wakeup call to the healthcare industry as a whole, yet sadly, the industry continues to suffer from poor cybersecurity implementation.
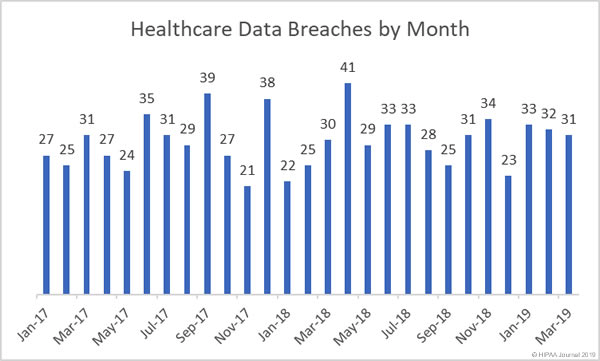
For the beginning of 2019, the healthcare industry saw 33 breaches in January, 32 in February, and 31 in March. If this trend continues, and we figure an average of ~32 breaches per month, 2019 will have the same amount of healthcare industry data breaches as previous years. Which means pretty much no improvement in cybersecurity for this sector.
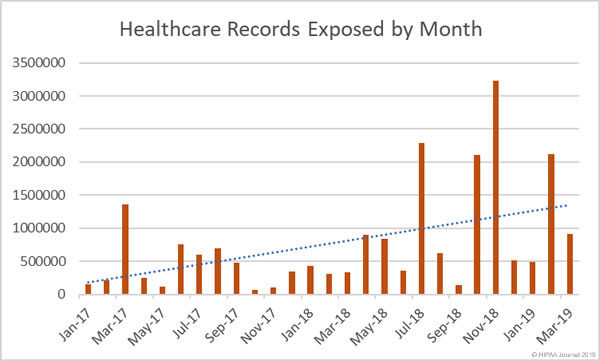
For the actual records exposed so far in 2019, the month of February saw the highest amount, with more than 2 million individual’s records exposed.
Before we talk about how to possibly stop this, let’s look at some of the biggest data breaches in recent past:
Major Breaches in 2019:
Navicent Health, Inc.
A healthcare provider which belongs to the Central Georgia Health System, and operates the second largest hospital in Georgia, U.S., fell victim to an email-based attack in April 2019. The impacted email accounts contained more than 278,016 individual’s records.
ZOLL Services LLC
In March 2019, this healthcare provider was attacked during a server migration. They estimate that 277,319 patients records were exposed, which was mostly patient names, birthdays, and limited medical information. However, ZOLL Services LLC noted that “A small percentage of patients also had Social Security numbers exposed.”, which is extremely troubling.
Other significant breaches in 2019:
| Name of Covered Entity | Covered Entity Type | Individuals Affected | Type of Breach | Location of Breached Information |
| Burrell Behavioral Health | Healthcare Provider | 67,493 | Hacking/IT Incident | Network Server |
| LCP Transportation, Inc | Business Associate | 54,528 | Unauthorized Access/Disclosure | |
| Superior Dental Care Alliance | Business Associate | 38,260 | Hacking/IT Incident | |
| Superior Dental Care | Health Plan | 38,260 | Hacking/IT Incident | |
| St. Francis Physician Services | Healthcare Provider | 32,178 | Hacking/IT Incident | Network Server |
| Palmetto Health | Healthcare Provider | 23,811 | Hacking/IT Incident | |
| Gulfport Anesthesia Services, PA | Healthcare Provider | 20,000 | Theft | Other |
| Women’s Health USA, Inc. | Business Associate | 17,531 | Hacking/IT Incident | Desktop Computer, Email |
Significant Breaches in 2018:
UnityPoint Health
A phishing attack was detected in 2018 on this health care company. Forensic investigation revealed multiple email accounts were compromised in a 2-month period, as employees were tricked by false business emails. The attack utilized a spoofed version of a trusted executive’s email account, and several employees responded to fake emails from the spoof account, supplying their own email credentials to the phisher’s requests. The compromised email accounts contained a total of 1,421,107 individual’s personal information.
MSK Group
This Tennessee-based network of orthopedic medical practices discovered their network had been breached around May 2018. This wasn’t a one-time ordeal, as it was revealed that parts of the network had been repeatedly accessed by hackers over a several month time period. The records of 566,236 patients were compromised, which included personal, health, and insurance information.
AccuDoc Solutions, Inc.
A billing company that operates the online payment system used by Atrium Health, which runs a network of 44 hospitals in South Carolina, North Carolina, and Georgia. They discovered that parts of their database had been compromised throughout September 2018, databases that contained the records of around 2,652,537 patients. AccuDoc reported that the databases were only viewed, not downloaded – a small comfort mostly for PR benefit, as there are several methods of copying data without actually downloading it. This was, in fact, the largest healthcare data breach to be reported in a number of years.
LifeBridge Health, Inc.
Malware was installed on the server of this healthcare provider based out of Baltimore, Maryland. The malware targeted the electronic medical record system used by LifeBridge Potomac Professionals, and LifeBridge Health’s patient registration and billing systems, which contained the data of 538,127 patients.
What Have We Learned, and What Can Be Done?
The major takeaway from all this, and perhaps the most obvious is that the healthcare industry does not take cybersecurity as seriously as it should. In fact, the healthcare industry spending on cybersecurity is absolutely abysmal, to say the least.
In a 2016 report from Symantec, a leading enterprise security vendor, healthcare companies are “notorious for their limited investments in cybersecurity.” ABI Research group backs up Symantec’s claims, as they found that “investments in the industry against cyber attacks will only reach $10 billion worldwide by 2020.” This is severely underwhelming, as other industries such as banking and financing allocate 12 to 15 percent of their total budget on cybersecurity tools.
There are two primary issues surrounding this problem.
The first is company accountability. Yes, there are penalties for HIPAA violations within the U.S., governed by the OCR (Office of Civil Rights). The OCR sets forth guidelines for data security practices in the HIPAA, and the OCR fines companies found to be in violation of the HIPAA security guidelines.
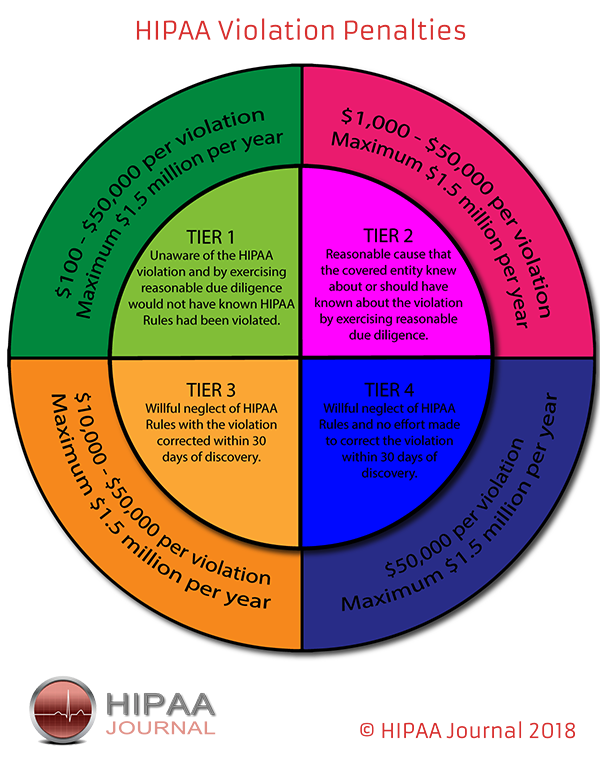
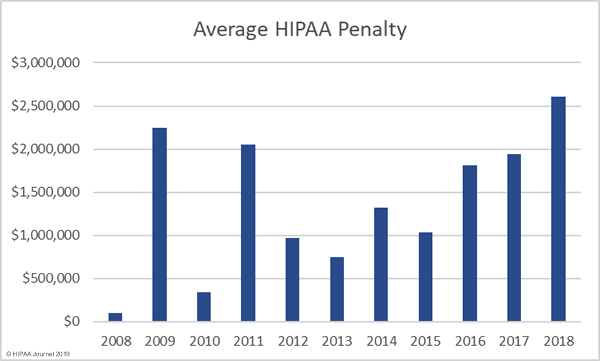
HIPAA Violations
While the penalties sound “severe” and can reach millions of dollars, they’re actually a drop in the bucket for many of the largest healthcare industry companies. See this chart of HIPAA violations:
As you can see, the fines and charges fall into 2 major categories. They are ‘Reasonable Cause’, and ‘Willful Neglect’. This is basically categorizing whether the company “didn’t know” they were in HIPAA violation, or they knew and didn’t care.
The problem is that the maximum fine 1.5 million per year, or $10,000 – $50,000 per violation. For smaller companies, yes, these can be damaging fines. For the largest whales in the ocean, however, these amounts are nothing. In fact, in some cases, it’s cheaper to pay HIPAA violations, than to invest in critical cybersecurity.
As Symantec reports, cybersecurity in the healthcare industry has usually been mainly a HIPAA compliance concern, meaning having just enough cybersecurity to be in compliance. Beyond that, it hasn’t been taken very seriously. However, in recent times, massive attacks on the healthcare industry, such as the WannaCry ransomware attacks in 2017, showed that hackers can completely paralyze healthcare companies and even shut down hospitals.
The problem here is that, even though more healthcare companies are beginning to take cybersecurity a bit more seriously, the cost of IT infrastructure for the healthcare industry is considerably higher than in other sectors. This is because of the specialized equipment and software that healthcare institutions utilize, and are expensive to maintain.
Understanding the Outlook for Cyberattacks on Healthcare Industry
So overall the situation is slowly getting better, but not fast enough. Attacks will continue happening as long as boards of directors consider cyber security as merely an IT or compliance issue, and not a legitimate business concern.
It’s a bit of a grim outlook, but things may get worse before they get better.
Learn more about our HIPAA compliant web hosting and HIPAA cloud hosting solutions.
This article was written for Atlantic.Net by Erika Rykun.