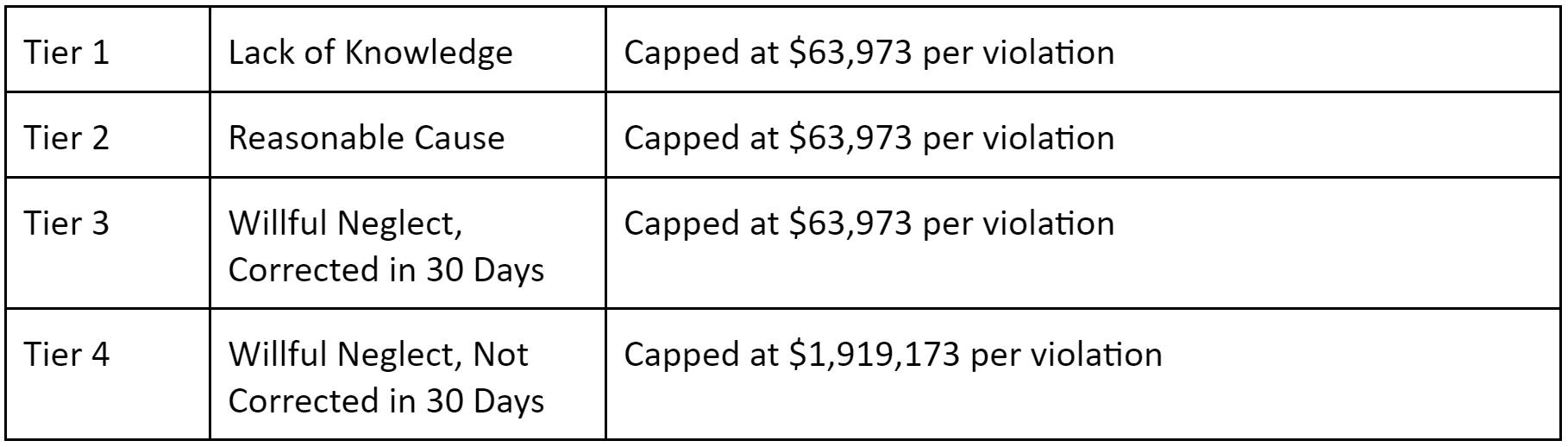Achieving and maintaining HIPAA compliance is a fundamental challenge to covered entities and business associates that are responsible for protecting patient health information. This responsibility is imposed on them by the stringent requirements of the Security and Privacy Rules of the Health Insurance Portability and Accountability Act.
Who Is Responsible for HIPAA Violations?
All healthcare entities and their associated businesses, such as managed service providers (MSPs), are jointly responsible for complying with HIPAA regulations. The agreement is enforceable by the U.S. Department of Health & Human Services (HHS) and can result in significant fines to all involved parties.
Q1 and Q2 2022 HIPAA Violations
Take a moment to browse the HHS hall of shame and you will see that violations are commonplace and can involve significant financial and reputational impact. Using data obtained from HHS for the first 6 months of 2022 (1st January 2022 – 30th June 2022), there have been 335 reported incidents to the HHS; these are incidents that have either been investigated or are under investigation by the HHS.
Over 20 million patients have been affected by reported breaches of HIPAA standards. Here are the Top 5 biggest breaches by the number of individuals affected.
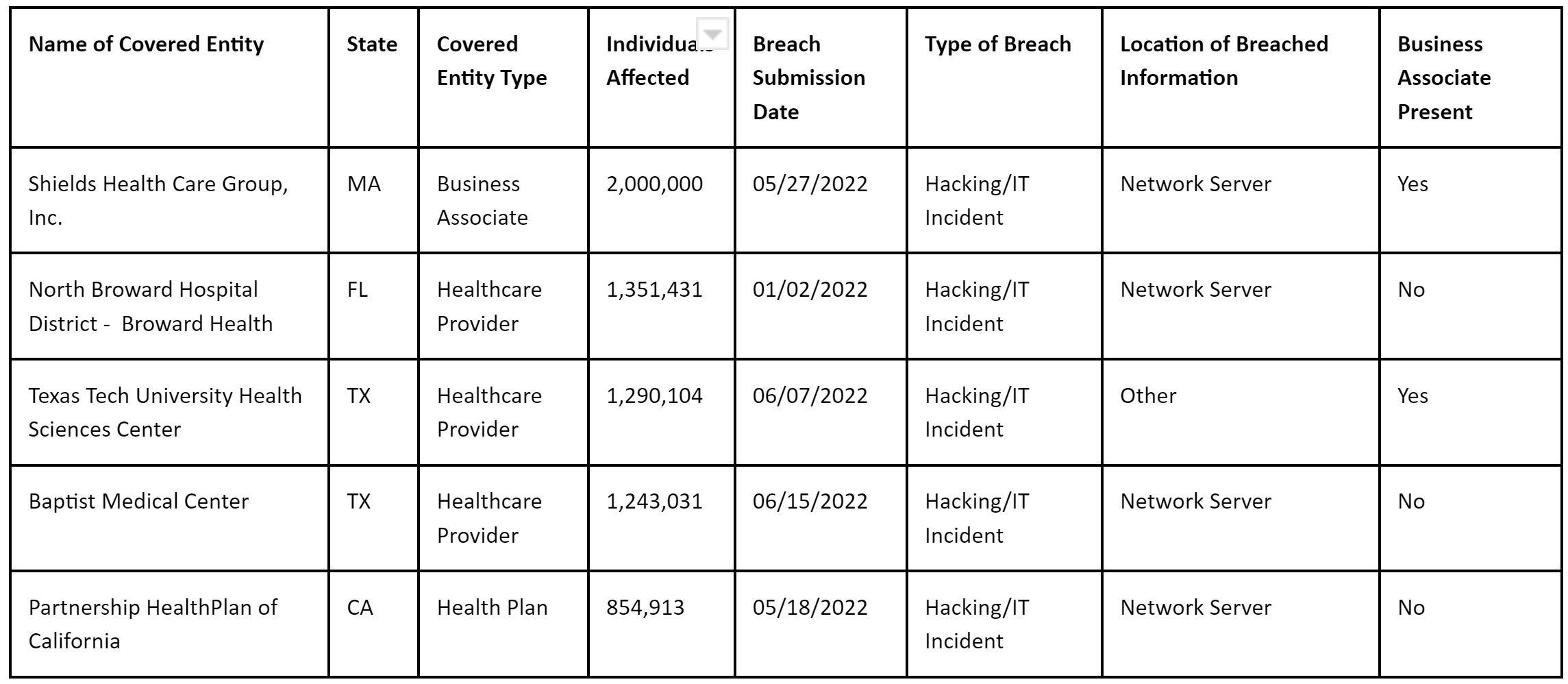
Source: HHS OCR Portal – Breach report
Violations are rarely the same, and not all incidents are as severe as the examples above. Nevertheless, in some cases, ePHI has actually been posted to the public internet, with patient files accessible directly via search engines. Understand that the severity of the fine will depend on the severity of the incident.
If your organization is found to be in violation of HIPAA, you might not necessarily have to pay millions of dollars because the penalty depends on the severity of the violation and the size of the organization.
How Are the Fines Calculated?
The OCR and the Centers for Medicare & Medicaid (CMS) are authorized to enforce penalties on HIPAA violations. The extent of settlements can be quite frightening, including civil and criminal judgments. Minimum and maximum limits were introduced in 2009, but according to the American Medical Association, the HHS “still has discretion in determining the amount of the penalty.”
There is one important exception: if the HHS determines that the covered entity was not purposely neglectful, one full month is given for the problem to be rectified.
HIPAA Violation Penalties
In 2022 the penalties and fines for HIPAA violations were amended by the HHS. The penalties are tiered around severity:
HIPAA Non-Compliance Criminal Penalties – Can You Be Imprisoned?
Sentencing can be more severe, though. Anything that violates the law and involves deception carries a maximum sentence of $100,000 and/or five years imprisonment. Violations that occur because an individual plans to use the data for their own gain or for malevolent reasons are penalized with judgments up to $250,000, accompanied by prison sentences as high as ten years.
Covered Entities & Individual People
The Department of Justice decided that if it is determined that a crime has been committed, covered entities (healthcare plans, data clearinghouses, and providers) can be held directly liable. Leadership in a covered entity can also be subject to criminal investigation and sentencing.
Even if someone in an executive position at a company where misuse takes place did not do anything that was specifically non-compliant, they still may be guilty as a co-conspirator or accomplice.
“Knowingly”
The Department of Justice specifically targeted a word within HIPAA crime provisions that is a source of confusion: what does knowingly mean?
Knowingly refers to the highest criminal penalty situation listed above, the “for their own gain” scenario (bolded above). According to Law360, “Under the statute, covered entities and individuals who ‘knowingly’ obtain or disclose individually identifiable health information with the intent to” profit from it or hurt someone face the stiffest penalties.
The Department of Justice has clarified that the word refers to knowledge of HIPAA law rather than knowledge of a particular instance of non-compliance.
Exclusion & Upholding the Law
The federal government can remove any healthcare plan, provider, or clearinghouse from the Medicare system if they have not adopted a universal, standardized medical code.
In terms of enforcement, OCR identifies and punishes HIPAA privacy violations. The Centers for Medicare & Medicaid (CMS) oversees the security and uniform code.
Choosing a Compliance Partner
The consequences of violating HIPAA can be extreme. Even if you are not fined millions, it is not a great way to spend money, and it’s not fun to end up on the HIPAA Wall of Shame.
For these reasons, it is extraordinarily important to choose a technological partner that specializes in healthcare HIPAA Compliant Hosting like Atlantic.Net. Our SSD Cloud Servers offer a 100% uptime guarantee and can launch in under 30 seconds.
What Happens If You Violate HIPAA?
Avoiding HIPAA violations is not as easy as it first may appear. If any employee violates certain stipulations, even unintentionally, the employer can be fined up to $1.5 million, the yearly cap per business.
The rules of compliance are complex, and a substantial number of technical, administrative, and physical safeguards must be adhered to, too.
Privacy and Security Violations
As you might expect, there are some trends in the type of violations of HIPAA compliance.
#1: Incorrectly Handling Data
Here are some of the most common breaches:
- Emailing an unintended person or party containing ePHI
- Sending an incorrect patient chart
- Choosing an incorrect dictator when sending transcriptions
- Select incorrect patient healthcare numbers, such as medical records, account numbers, or identification numbers
- Inputting an incorrect doctor
- Disclosing healthcare information to third parties without consent
- Waiting or generally neglecting to notify compliance officials or other appropriate personnel of any possible data breaches
- Throwing away confidential healthcare documents in an unauthorized way (making them susceptible to theft)
Regardless of whether or not an individual or facility has the right to review the record, there must still be a justifiable reason associated with each instance of access.
#2: Contractual Errors
Here are some of the most common breaches:
- Accepted patient authorization forms that have missing data:
- missing the full name of the patient
- no entity defined to which health records are to be released
- elements of PHI/EMR (electronic medical records) that have not been cleared release
- end date through which permission is granted
- Omitting a clause related to revocation (a right that needs to be clearly stated on a HIPAA authorization form for it to be legitimate)
- Neglect to sign updated business association agreements (BAAs) with all applicable third parties
- Disclosing patient data beyond the dates established in the relevant HIPAA contract, which typically involves an employee failing to double-check the authorization prior to release
- Using laptop or PCs to store PHI without any appropriate security solutions installed (this is the most common violation and can be solved by HIPAA-compliant cloud hosting)
How to Avoid HIPAA Violations
You now know the most common violations, so what can be done to protect your business interests?
#1: Secure PHI and EMR
Establish one password to get access to the data, and designate a compliance officer on your staff (if you have not already) to safeguard the password. Adjust the password frequently, ideally with random password generation software, and use two-factor authentication for access.
#2: Creation/Development Of Protective Policies
Create management policies to make it less likely that patient health information gets into the wrong hands. Notify all personnel that any instances of entry into the EMR database are logged and monitored, and supply appropriate training as needed.
#3: Simple And Timely Patient Access
HIPAA requires that patients be able to review their EMR whenever they desire. Usernames and temporary passwords can be supplied to all patients immediately, both for compliance and efficiency.
#4: Noncompliant disposal of hard copy PHI
HIPAA places a significant focus on digital communications, but controlling paper copies of EMR is critical as well. You want to either have all paper documents under lock and key, accessible only to the appropriate staff members, or to keep all the paperwork at a fully secured external location. Shredding of any paperwork for disposal should either be conducted in-house (with extreme care) or through an expert third party.
HIPAA Violations 2022: Atlantic CEO Q&A
The Becker’s Healthcare Review interviewed our very own Marty Puranik, the president and CEO Atlantic.Net. The Q&A was about the evolution of HIPAA legislation and how healthcare organizations can prevent data breaches.
How Can Healthcare Organizations Prevent Data Breaches?
“It is a good idea to identify someone within your organization who will be responsible for training that will cover common internal and external breach risks, along with HIPAA-compliant policies and procedures to mitigate the threats to ePHI. Your staff needs to understand that health data can never be disclosed on social media or via text message and that it’s not all right to access ePHI simply out of curiosity. Patient files and mobile devices should be protected carefully at all times and, as your risk assessment reveals, target the high-priority risks immediately.”
Can you explain how you have seen HIPAA evolve over the years?
“One of the main things is that the fines were raised significantly. The maximum annual amount that could be charged per provision has increased from $25,000 to $1.5 million. Another core aspect of compliance introduced in HITECH was the Breach Notification Rule, which made it necessary to contact patients impacted by breaches directly and, in some cases, through the media. Another key change is that HIPAA rules became directly applicable to business associates. The main concept for staying well-versed in compliance is to get help as needed. While in-house training is great, you may also benefit from working with HIPAA-compliant service providers or consultants.”
What Is Considered A Data Breach?
“Unauthorized use or disclosure of electronic protected health information is a breach. There are three exceptions:
- If the ePHI was accessed “in good faith” by a person who was acting on behalf of a HIPAA-compliant organization
- If it was disclosed by an authorized individual to an unauthorized individual at the same organization
- If the organization from which the information was accessed has a reasonable belief that the unauthorized party would not be able to collect and keep the data
The ePHI also must be unsecured in order for it to be a breach. Determining quickly if a breach has occurred allows you to send mandated notifications and take other first steps.”
How Can Healthcare Organizations Use Technology to Protect Their Patients’ Health Data?
“Technology is integral to HIPAA compliance since it is directly related to the security rule, which essentially applies the Privacy Rule to IT. There should be encryption for both in-transit and at-rest data, for instance, SSL certificates should be installed. Backups are used to maintain availability requirements under the law.”
“The backups you use should be offsite CDP backups that allow you to completely restore your information using an up-to-date, easily accessible remote copy. Firewall and multifactor authentication are also critical to maintaining security, and we recommend those as managed services.”
How Do See The Healthcare Landscape Changing In The Coming Years?
“The Office of the National Coordinator’s contest for blockchain advances shows how it is being embraced at the federal level, in part because it helps address interoperability. Blockchain becomes even more important with the growing interoperability challenges of wearables and the IoT.”
“A study from earlier this year showed the average breach sector-wide costs just over $700,000, so it is an unexpected expense for which you get billed the better part of a million dollars. Clearly, that will restrict the growth of a company; the combined effect of these breaches has an impact on all aspects of healthcare, and the ASC space is no exception. The ASC sector is projected for 6 percent growth for the next few years despite the threat landscape.”
“The insider threat is the most common reason for a breach, per a study released earlier this year. Since that’s the case, there should be increased awareness that strong healthcare security preparation – setting aside compliance for a minute – is about looking within as much as it is about looking without. Now, most of these incidents are human error, so we are not generally talking about malice. Nonetheless, the results are the same.”
Take Advantage Of HIPAA-Compliant Business Associates
HIPAA violations are costly, and staying compliant represents a time-consuming hassle for many healthcare organizations. Using fully HIPAA-Compliant Hosting solutions can remove the stress by allowing a company with three decades of data center expertise to stand guard over your PHI. We offer a full line-up of 100 percent HIPAA-Compliant Cloud Server solutions.