While achieving HIPAA-compliant status has always been a significant accomplishment for cloud hosting providers, organizations that process electronic Protected Health Information (ePHI) for the purposes of business continuity and disaster recovery recently had two major constraints added on top of HIPAA compliance requirements.
Healthcare organizations, business associates, and third parties already must adhere to a stringent set of data handling regulations enforced ever since the enactment of Health Insurance Portability and Accountability Act (HIPAA) in 1996. More recently, new data privacy requirements have been passed in the European Union (EU) and the state of California that have added further restrictions on data processing and data handling.
Game-Changing New Regulations
The California Consumer Privacy Act (CCPA) and the General Data Protection Regulations (GDPR) are both recently passed privacy acts that update antiquated laws in relation to how personal information (PI) is handled, stored, and processed. Since the proliferation of Internet services, mobile telecommunications, and social media, campaigners have been demanding changes to how businesses handle PI.
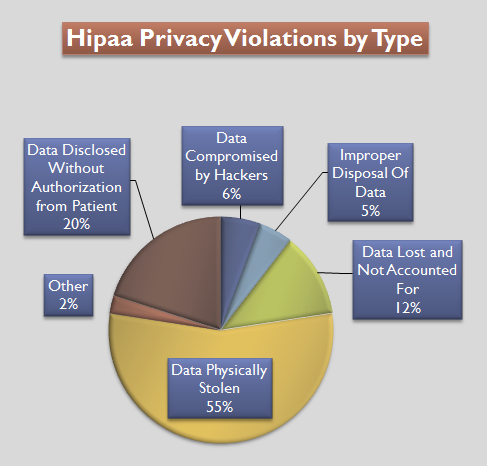
Hipaa Violations by Type – Pie Chart
CCPA was passed in 2018 and came into force on January 1, 2020. GDPR was passed into law on May 25, 2018. Both legislations have similar recommendations and requirements, but GDPR is focused on European citizens’ personal information while CCPA relates to US citizens’ personal information.
Importantly, both legislations have a shared synergy that impacts businesses on both sides of the Atlantic. Any business in the United States that is responsible for processing European personal information, and any business in Europe that processes US personal information, must adhere to each of the new legislation guidelines to be compliant with the updated privacy rules.
To briefly summarise GDPR, some of the key protections introduced are:
- GDPR requires that permission must be granted prior to collecting data. This is why you now see “Accept All Tracking Cookies” popups when you enter your favorite websites.
- You must notify of a data breach within 72 hours.
- Upon request, data collectors must be able to explain what information is being collected, how it is being used, and whether the data is being shared.
- EU citizens have the right to have any and all data held on them deleted by the collector.
The CCPA protections are largely the same as GDPR, and some of the key elements are:
- US citizens have the right to know what personal information is being collected, sold, or disclosed.
- US citizens have the right to view their collected data and demand their data is not sold.
- CCPA applies if a company generates more than $25 million USD a year and half of that revenue is from selling personal data.
For those trying to balance HIPAA compliance with the requirements of these two new pieces of legislation, pay attention – here is the important information you need to know.
When Data Disaster Strikes
HIPAA compliance requires that an organization must develop a contingency plan that allows an organization to both protect ePHI and quickly recover core business functions in the event of a disaster. Disaster recovery is an information technology safeguard designed to protect both the business operations and the access to ePHI. The ability of a healthcare facility to be able to resume day-to-day activities and process ePHI is an essential part of compliance.
For a quick example, let’s consider a hypothetical hospital whose infrastructure has been infected with ransomware. Without normal access to patient medical records, one would expect the business operations of the hospital to grind to a halt quickly. HIPAA regulations were created to combat such an “Armageddon” scenario, meaning that the hospital could fail over technical services to a secondary location, thus restoring access to core applications and ePHI.
When the U.S. Department of Health and Human Services (HHS) created the HIPAA act, it is unlikely that they could have predicted what future local or international privacy rules might be introduced and their impact on US legislation. Likewise, GDPR and CCPA legislation was focused on protecting data privacy online, but was seemingly not tailored with the medical industry in mind.
The Problem with Duplicate Data Centers
Prior to the recent legislation, a favorite disaster recovery solution to protect data was to simply create redundant data center(s) in different geographic location(s) or to contract a colocation facility. The end result is that if the onsite database becomes unavailable due to a malfunction, it is often a simple matter to switch over production services to the secondary location.
Complications arise due to the fact that both GDPR and CCPA require that all personally identifiable information related to any person in the database can be removed upon request. Handling these requests and securely wiping the requested data has to be done not only on the live database, but also any replica copies.
Healthcare organizations and cloud service providers are having to create automated processes and routines that identify expired data and delete what is out of scope. The business associates must work together to identify data that is in scope, as well as understand how long the data can be retained to remain compliant. The end result of these additional requirements is more work and an increased chance of mistakes, and this might place the entire organization in violation of the new regulations if not done correctly.
The Problem of Unstructured Data
When it comes to protecting or deleting personal information, such as, in one example, a Social Security number from the Social Security Administration’s database, the task to achieve this is not overly complicated. This is because a Social Security number is structured data that is easily located within a database.
Unstructured data, such as documents, emails, form submissions, excel files are much more complex. The reason is that these files might contain Protected Information, and it would be an administrative nightmare to audit every single file for sensitive information. This problem makes precise analysis and location of personal data a huge challenge.
Advanced tools can be deployed that encrypt data at rest and in transit, or use AI to redact information buried in documents. In one popular example, if an administrator accidentally sent a manual payment receipt to a patient and the PAN was not hashed out, intelligent email software can identify this information in email attachments and reject sending of the email, automatically responding to the sender that their action would breach GDPR or CCPA regulations. However, the implementation of these toolsets is technically challenging and expensive to achieve.
The Right to be Forgotten
Prior to GDPR and CCPA legislation, some speculated that personal privacy may have already been dead – check out this article about Amazon Alexa if you don’t believe it – but the foundations of both the GDPR and CCPA rest on the idea that an individual has the right to be forgotten. In other words, any website or business that holds your information in a database is required to delete it upon request.
This newly outlined right often clashes with practical business processes in reality. A good example is bank loans. Does it make sense that you can ask your banker to get rid of all your data he or she has on file immediately after you’ve taken out a $250,000 loan? Probably not.
The right to be forgotten directly impacts disaster recovery services, creating an almost impossible situation for business associates. HIPAA legislation demands that the location of ePHI is known explicitly to all involved. However, the reality is that many medical professionals do not have a firm grasp on what ePHI data that they do have, which makes the process of reliably deleting requested records an exercise in futility.
The added complication makes choosing the best HIPAA compliant hosting partner an essential due diligence exercise the healthcare organization must undertake. The right partner can help to guide healthcare professionals in achieving compliance and knowing exactly what ePHI data is in the scope of the legislation.
Hackers Create a Huge Liability
It’s one thing if an earthquake, hurricane, flood, or tornado were to take out a hospital’s frontline database. Such “acts of God” are unavoidable. But if you own one or more of the 1.24 billion websites active online now, you have to be even more worried about human intrusion, which presents a greater danger when measured against the standards set out by these new regulations.
Cyberattacks that leave behind malware and steal personally identifiable information are often preventable. The responsibility lies with the organization and technology business partners, and failure to uphold this responsibility can bring a heavy financial penalty.
European 451 Error Code Example png
For example, the first year GDPR was active yielded $344 million worth of fines that mostly fell in the category of “insufficient security measures.” GDPR penalties for a single incident can run as high as $20 million euros or 4% of global income, whichever number is higher. That’s a hefty fine to be dropping on top of an organization that is already reeling from what might have been a costly security breach.
Final Thoughts
Disaster recovery remains a critical part of HIPAA compliance, and healthcare organizations and their technology partners must be able to create a disaster recovery solution that protects ePHI, as well as the core applications that process and maintain ePHI, at all times.
In-scope ePHI must be identified, and its locations documented, within a Business Associate Agreement (BAA). The technology partner and the healthcare institution must work together to ensure ePHI is protected at all times. GDPR and CCPA require explicit consent to access ePHI, but HIPAA allows anonymized data to be made public.
The rules are slightly different when reporting a data breach to the authorities. HIPAA demands that the Officer for Civil Rights (OCR) must be informed for breaches of 500 or more patients within 60 days, while for GDPR there is a 72-hour breach reporting window.
From the preceding analysis, it’s easy to see why cyber insurance has become an increasingly popular solution. In theory, cyber insurance could protect an online company by paying off fines imposed by regulators. There are mixed opinions on this type of protection; for some, it adds peace of mind, while for others it provides protection when inadequate information technology is available.
For now, any organization under the auspices of HIPAA would do well to find a security expert with some track record of success in navigating the current regulatory minefield.