What is ransomware?
One of the fastest and most damaging cyber security threats falls under a category called “ransomware.” Ransomware is malicious code that encrypts all the user’s files and is usually downloaded unknowingly. This type of malware gets its name from what it does when a user tries to open an infected file: it prompts the user to pay a ‘ransom’ within a timeframe to receive a decryption key, which would then allow you to decrypt your files.[1] Even if you choose to pay the ransom, there is no guarantee you will gain access to your data. In this article, we will explain steps you can take to protect and secure your environment.
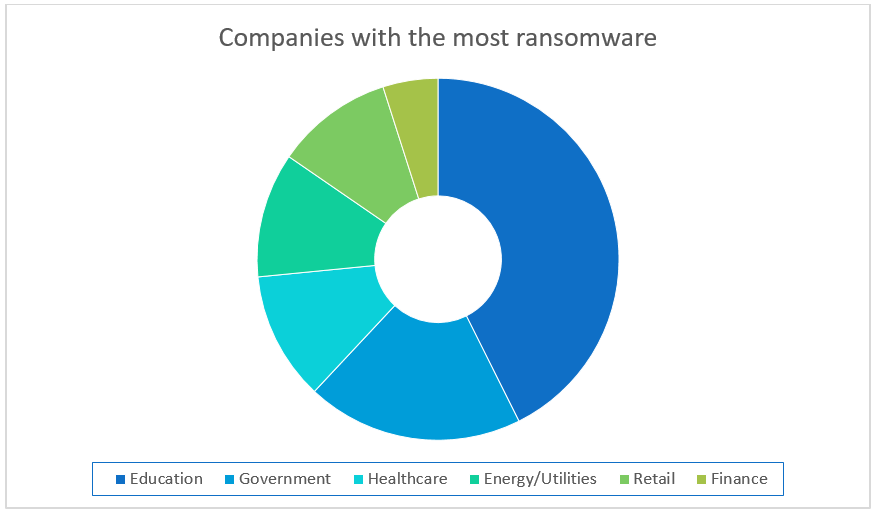
Ransomware by Numbers
Ransomware is a real threat to any business that allows user access, as it depends on users to spread it. Different industries also have different risks, with healthcare usually opting to pay the ransom to protect patient data, while the education industry has the highest rate of infection. Other lucrative targets include classified documents, financial documents, and intellectual property[2]. With names like Telecrypt, iRansom, FSociety, and CryptoLuck, the goal of ransomware is all the same for their creators: making money. According to Lavasoft, the CryptoWall 3 ransomware cost users $325 million just in 2015 alone.[3] As ransomware grows and evolves, they become even more costly. At the end of 2016, one of the most harmful ransomware is named “Cerber.” Not only does it lock your files from being accessed, but recent variations have incorporated the stealing of personal information and scripts that cause your machine to target other servers.[4]
Source: https://info.bitsighttech.com/bitsight-insights-ransomware
E-mail 101
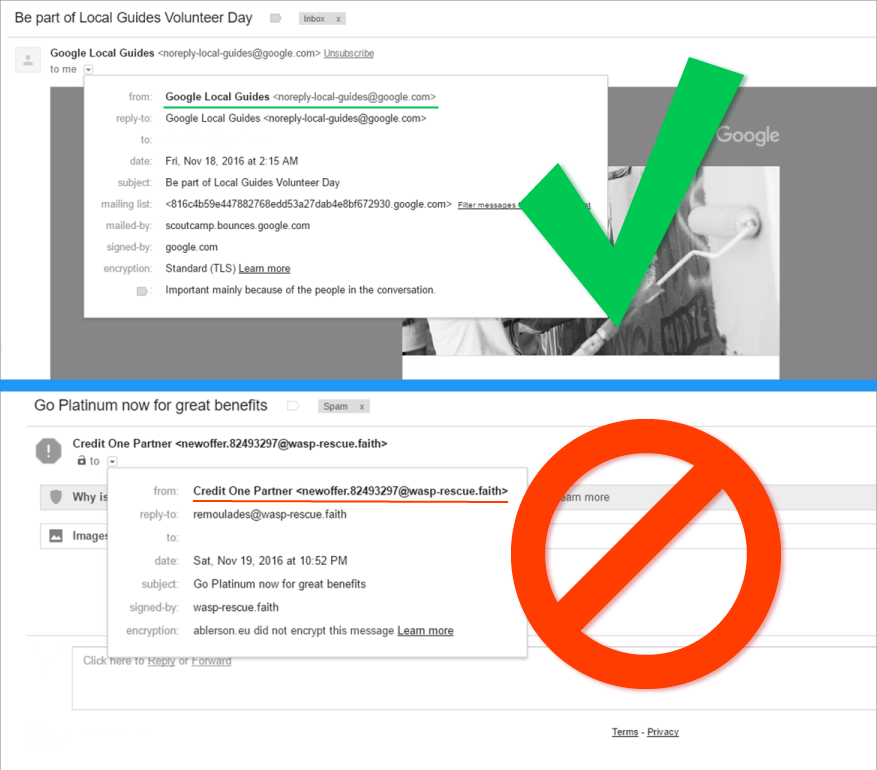
According to a study by BitSight[2], the majority of ransomware comes in the form of email attachments that contain malicious weblinks or infected document attachments. They may look legitimate to the lay-user, but a deeper look often reveals the truth. Below are some tips on what to look out for when viewing email:
- Verify the sender’s email address. Many of these malicious emails look like they are actually coming from a credible source. If you did not ask for the email, you should verify that the email address the user is sending from belongs to the right source. For example, in Gmail you can visibly see that one of the two senders below looks a little phishy.
- Don’t open attachments you did not ask for. The general rule is to never download an attachment unless you have specifically asked for one.[5] Most companies are not going to send you an email with an attachment because of its unsafe nature. If it is an invoice or statement, check to see if it is available by logging into the company’s website. If you are in doubt over any attachment that you know you did not ask for, double check with the company or person who sent it.
- Watch out for suspicious subject lines. Subject headers such as ‘FedEx Delivery #352’ and ‘PayPal Unusual Activity’ are just some examples of emails that should raise suspicion. The easiest way to verify if these emails are legitimate is to make sure it is being sent from one of those companies. PayPal, for example, will always send from “@paypal.com.” They would not send any email from a random email address.
- Trust no one. Here at Atlantic.Net, we see accounts being compromised daily, so it is important to remain vigilant, even if the email comes from someone you trust. If it seems suspicious, verify with that person to make sure what they sent you is legitimate.
- Don’t just ‘click here.’ Web links may appear legitimate also, but it is important to always be aware of the source, and destination, of such links. The easiest way to know where a link goes to is to right-click on the link, copy, and then paste it into a text editor. Some email programs also support hovering your mouse over the link to see its full website address. If you are not familiar with the source and were not expecting an email from the source, the best thing to do is to log in to that website the way you would normally.
Tackling Ransomware
Before considering how to tackle a potential ransomware issue, it is important to understand some of the most significant challenges that infected users face:
- Out-of-date protection. Some older antivirus/malware software may be out-of-date. Even worse, some are not even designed to detect ransomware.
- Network file shares. An infected customer’s issue with ransomware can easily become a widespread problem: NFS’s, or network file shares, that allow users to access more files than they need can easily spread very fast, affecting everyone else’s files.
- Limited solutions. Once infected, victims of ransomware attacks have very limited options available to them when it comes to recovering files. The best solution is to restore all files from a backup point that is not infected.
Be Proactive with Trend Micro Deep Security
At Atlantic.Net, we have partnered with Trend MicroTM to offer an all-in-one, enterprise-grade security solution. Their Deep SecurityTM solution provides enhanced protection for virtual, cloud, and physical servers. Through this solution, we can provide a broad range of features that not only detect malicious software (including ransomware), but immediately stop it.
Trend Micro Deep Security is available as an add-on for all Atlantic.Net Dedicated and Managed Cloud customers.
For more information on how Trend Micro Deep Security protects you, click here.
Prevent Data Loss with Enterprise-Level Backups
Should your servers become infected with ransomware, having backups can protect you from losing data or having to pay to access your data. At Atlantic.Net, we believe the best practice for your environment is to have redundant backups in geographically-independent locations. What does this mean? It goes back to the old saying of never putting all your eggs in one basket.
Atlantic.Net offers two backup solutions, depending on your hosting setup:
For Dedicated Servers, we currently deploy a Server Backup Management solution from R1Soft. R1Soft’s backup software performs a block-level backup that directly reads data from the disk. Block-level backups are performed in the background and allow for minimal system overhead. Backups are also supported for virtual machines running on our Microsoft Hyper-V or ProxMox dedicated virtualization hosts. In circumstances where you are infected, R1Soft enables us to do complete system restores that will have your system up and running within hours.
Atlantic.Net’s Cloud Servers can be set to backup daily. Should anything go wrong with your Cloud Server, you can easily select any of the daily backups to restore to and be back up in minutes. This feature can easily be enabled within our Cloud Portal, and we store up to 30 days of backups.
How Atlantic.Net Can Help
Through awareness and education, you can help minimize the risk of being infected with ransomware, but the risk is ever-increasing. With bigger data comes more responsibility and as your hosting partner, Atlantic.Net has the expertise and industry-leading infrastructure to minimize the risk of data loss. By employing both preventative measures, like awareness and real-time security monitoring software, and proactive measures, like full daily system backups, we can work together to harden and secure your environment.
To speak with a sales representative on how Atlantic.Net can protect you from ransomware, please contact [email protected].
[1] http://www.hhs.gov/sites/default/files/RansomwareFactSheet.pdf
[2] https://info.bitsighttech.com/bitsight-insights-ransomware
[3] cryptowall ransomware cost users 325 million in 2015
[4] ransomware recap nov 7 18 2016
[5] 8 tips for preventing ransomware/