Table of Contents
- What Is a Database?
- 1 - Understand what HIPAA is.
- 2 - Know core tools for protecting a HIPAA-compliant database.
- 3 - Train your staff.
- 4 - Examine your infrastructure for technical and physical safeguards.
- 5 - Limit access to applications and data.
- 6 - Set up data usage controls.
- 7 - Encrypt your databases.
- 8 - Monitor use of the database and create logs.
- 9 - Decide whether you want to use an outside party.
- 10 - Choose a partner with niche HIPAA expertise.
If you’ve been charged with implementing a HIPAA-compliant database and it’s your first time building a system that adheres to the healthcare law, you may feel overwhelmed and confused about where to start. The first step is to focus your efforts so you can move forward systematically in creating one. The below considerations will allow you to establish a database and protect it over time.
First, let’s explore some background information about databases, take a look at two popular database solutions, and understand how they relate to HIPAA compliance.
What Is a Database?
Database systems are an essential business application for the healthcare industry, and almost all applications, websites, and proprietary healthcare tools will read and write data from some form of a database. Two of the most popular database applications used today are MySQL and MS-SQL.
What Is MySQL?
MySQL is an Oracle-based open-source relational database that is most commonly found installed on Linux Operating Systems such as Red Hat, CentOS, and Ubuntu.
What Is MS-SQL?
MS-SQL, also known as Microsoft SQL Server, is a very popular database for Windows Server users. Recently, Microsoft has ported MS-SQL to Linux, and you can also get MySQL on Windows.
Securing Database for HIPAA Compliance
A database is used to store tables of structured or unstructured data. It is an essential tool for healthcare organizations, and due to the very nature of a database, the chance of electronic Protected Health Information (ePHI) being saved in a database is very high.
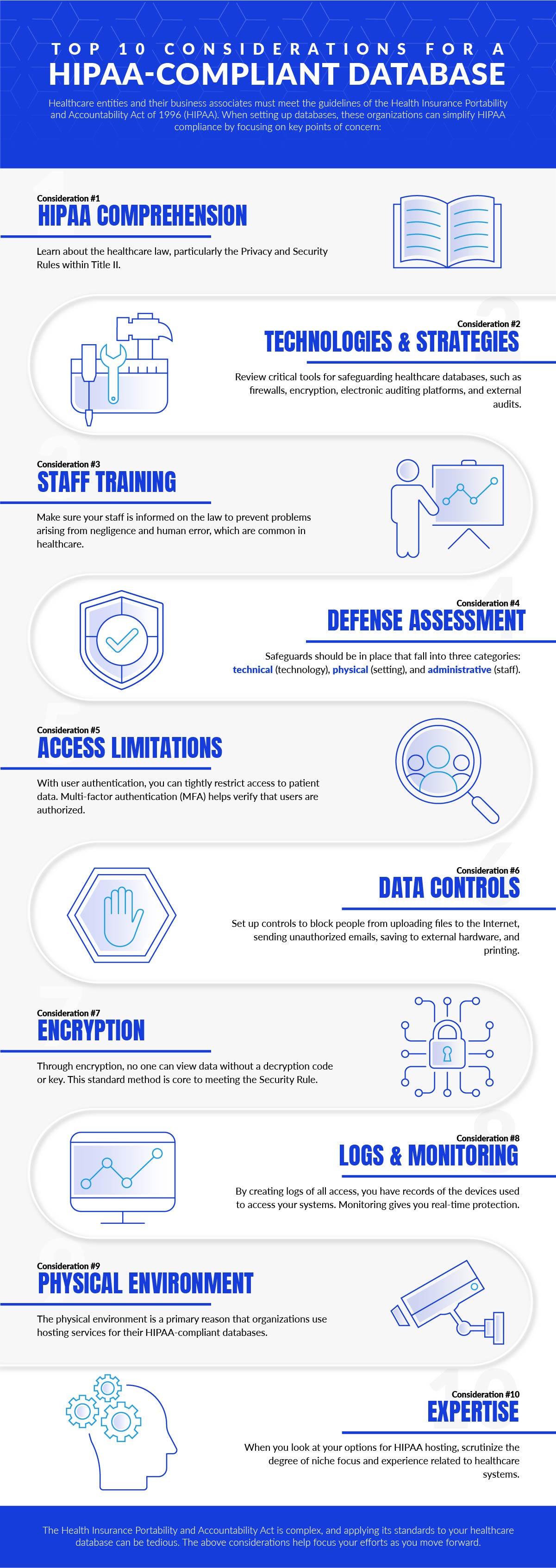
As a result, securing MySQL and MS-SQL Databases is a primary concern. Here are our top 10 considerations for implementing a database for your practice while adhering to the physical, technical, and administrative safeguards of HIPAA Compliance.

1 – Understand what HIPAA is.
The Health Insurance Portability and Accountability Act (HIPAA) is a law that was passed in 1996 by the United States Congress. This law is wide-ranging but is focused on:
- allowing for US employees and their families to maintain their health insurance coverage if they leave jobs or change to new ones;
- preventing abuse and fraud within the healthcare industry;
- introducing standards for healthcare data that should be used with billing and in other contexts; and
- mandating that data should be properly safeguarded and that its privacy should be maintained.
That fourth point is the key concern when protecting a database. (See the Privacy Rule and Security Rule of HIPAA’s Title II, particularly the latter.)

2 – Know core tools for protecting a HIPAA-compliant database.
Key tools you will use in order to protect your database include data encryption, firewalls, electronic auditing systems, and third-party audits. Data encryption is used to make certain that only the person or organization authorized to see the HIPAA data can see it. It protects healthcare information both when it is being stored and during its transmission. Firewalls are software programs that block illegitimate access to networks and prevent access by unauthorized individuals. Electronic auditing platforms necessitate that people must use login credentials for access and create a log of everything each individual does. Finally, third-party audits give you perspective by bringing in someone who focuses specifically on HIPAA compliance. By bringing in an outside auditing agency, you can reveal any weaknesses you might have so that you can make corrections right away.

3 – Train your staff.
You should maintain compliance not only through technology but through your staff as well. Healthcare is a field that is particularly susceptible to problems arising from human error and negligence. Any mistakes made by human beings could have extremely expensive outcomes, so that aspect of compliance cannot be forgotten. Training will allow any of your personnel who are handling protected health information to do so in a manner that is consistent with the law and that properly protects sensitive healthcare data.

4 – Examine your infrastructure for technical and physical safeguards.
When you set up a HIPAA compliant database, you may use your own data center or the facility of a HIPAA compliant server hosting provider. Either way, it is critical that technical and physical safeguards are in place (beyond the administrative safeguards that relate less directly to the technology).
Technical safeguards are designed to secure electronic data. The technical methods that you need in place to be HIPAA-compliant include integrity controls, audits, user identification, authentication, and encryption/decryption. These parameters will also help to define the steps that are taken for electronic health access when an emergency or natural disaster strikes.
Physical safeguards have to do with validation and access for in-person interaction with equipment that contains electronic PHI. These defenses control the people that are able to make any kind of contact with servers and computers on which electronic patient data is stored. The protections additionally contain standards for disaster recovery in the event of natural disasters or other extreme, unexpected events. They also include the manner in which electronic health records should be used and removed from the system. For instance, there should be a set of steps in place to dictate how malfunctioning hard drives are removed.

5 – Limit access to applications and data.
Another consideration is how you want to go about limiting access to healthcare applications and data within your environment. Access is a core consideration because you will improve security by limiting application and patient record access to those employees who need that access in order to complete tasks. When you restrict access, you will leverage user authentication, which will protect your patient information by verifying that all users who look at the data have been authorized. It is a very good idea to set up multi-factor authentication (MFA) to control access so that users will have to confirm their identity through multiple forms of validation.

6 – Set up data usage controls.
The data controls that you implement should be extensive, not just monitoring and limiting access, but checking proactively in order to block malicious efforts as they emerge. Data controls could be used to stop various types of actions related to ePHI, including printing, copying files onto external drives, email transmission without authorization, and online uploads. In order to know that proper identification and tagging of your ePHI can occur so that it can be safeguarded, use best practices for data discovery and classification.

7 – Encrypt your databases.
Encrypting your ePHI will convert your data into an encoded form. By encrypting, you make it only possible for someone to see the data if they have a decryption key or code. Encryption is a strong method that can be used to make sure that electronic health records are not compromised by nefarious third parties.
Encryption helps meet the parameters of the HIPAA Privacy and Security Rules but is especially a focus of the latter, which is centered on electronic protections. The Security Rule requires that covered entities under HIPAA protect all data they generate, send, store, or receive, and encryption is a standard way to shield the data from anyone who is not intended to view it.

8 – Monitor use of the database and create logs.
Setting up logs that record all access and applicable data makes it possible to know the locations and devices from which access is being obtained, as well as the times, applications, and specific data that is being accessed. You can benefit from logs during audits when you can bolster your defenses by looking at issues that have been exposed by the logs. When you experience a security event, you can find out the points of entry, why the intrusion occurred, and estimate the damages that you have sustained using an audit trail.

9 – Decide whether you want to use an outside party.
As indicated above, you can use your own data center or hosting service – cloud or otherwise – to establish your HIPAA-compliant database. It is certainly easy and convenient to be able to meet compliance standards when they are already built into a purpose-made hosting solution by an expert third party. In fact, choosing to work with a host is more compelling when you think beyond ease of management to physical security. It is easy to forget the physical as you deeply consider the technical considerations of a HIPAA-compliant system; physical security breaches are still a major threat. Not only could you have an intruder, but you could have devices or data stolen by disgruntled employees; and no matter whether the physical loss is due to an internal or external actor, it is one of the top data breach vulnerabilities.

10 – Choose a partner with niche HIPAA expertise.
If you are concerned about setting up a HIPAA database that will store electronic health data, using an outside host for your systems can be wise. There are many hosting plans from which to choose, some of which have more experience with HIPAA than others. At Atlantic.Net, healthcare is one of our primary points of focus and has been for years. HIPAA Compliant Database Hosting by Atlantic.Net is SSAE 18 SOC 1 & SOC 2 certified and HIPAA & HITECH audited, designed to secure and protect critical healthcare data and records. See our HIPAA-compliant hosting solutions.
Read More About HIPAA IT Compliance
- HIPAA IT Compliance Guide
- Best HIPAA Compliant Fax Service
- Best HIPAA Compliant Email Service
- Best HIPAA Compliant VOIP Service
- What Is a BAA?
- SSAE16, SAAE18, SOC1, SOC2 – Why You Should Care
- Best Healthcare Software Development Companies
- Best HIPAA Consulting Companies
- Is It HIPPA or HIPAA?