Table of Contents
- HIPAA-Compliant Hosting Services Checklist
- First-Class Healthcare HIPAA Hosting vs. Standard Hosting: What’s the Difference?
- Responsibilities for Safeguarding Electronic Protected Health Information Are Defined by the HIPAA Final Rule
- What Is HITECH?
- What Are Examples of Covered Entities and Business Associates?
- HIPAA Violations Can Result in Jail Time
- Top 11 HIPAA Fines by Settlement 2014-2024
- The HHS Audit Program
- What Is the HIPAA Security Rule?
What should you look for in a good HIPAA-compliant hosting provider? Healthcare hosting providers must comply with HIPAA, the Health Insurance Portability and Accountability Act of 1996, which means they must protect and secure patient records. When you look at HIPAA-compliant hosting providers, you want to know how HIPAA audit-ready the healthcare host is.
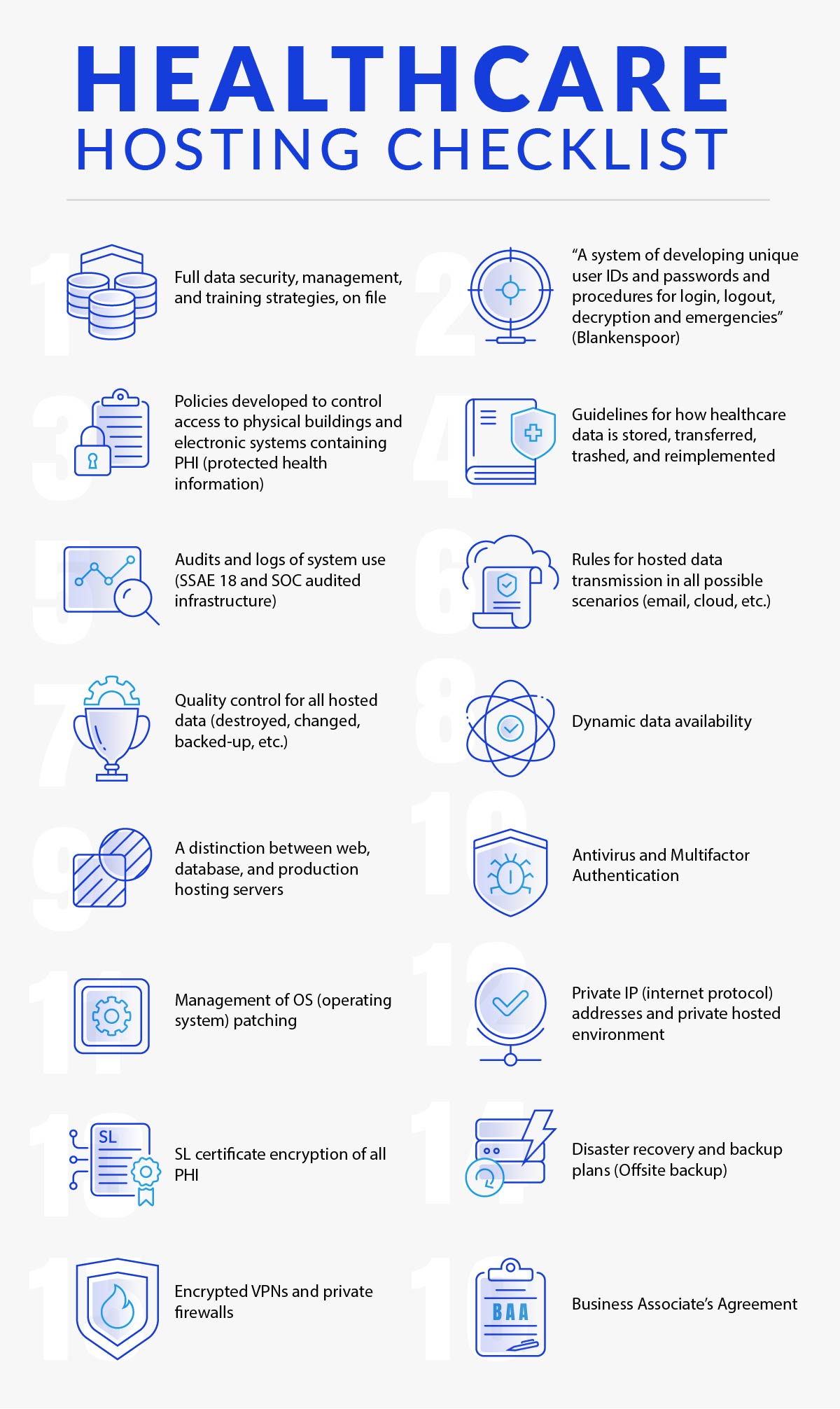
HIPAA-Compliant Hosting Services Checklist
The first step to ensure HIPAA compliance from your web hosting service is reviewing HIPAA-compliant hosting requirements with this handy 16-piece HIPAA Server Hosting Checklist (which covers the basics but is obviously not substantive enough for a comprehensive HIPAA compliance evaluation):
- Full data security, management, and training strategies, on file
- “A system of developing unique user IDs and passwords and procedures for login, logout, decryption and emergencies” (Blankenspoor)
- Policies developed to control access to physical buildings and electronic systems containing protected health information (PHI)
- Guidelines for how healthcare data is stored, transferred, trashed, and reimplemented
- Audits and logs of system use (SSAE 18 and SOC audited infrastructure)
- Rules for hosted data transmission in all possible scenarios (email, cloud, etc.)
- Quality control for all hosted data (destroyed, changed, backed-up, etc.)
- Dynamic data availability
- A distinction between web, database, and production hosting servers
- Antivirus and Multifactor Authentication
- Management of OS (operating system) patching
- Private IP (internet protocol) addresses and private hosted environment
- SSL certificate encryption of all PHI
- Disaster recovery and backup plans (Offsite backup)
- Encrypted VPNs and private firewalls
- Business Associate’s Agreement
Click here to find out more information on HIPAA hosting.

First-Class Healthcare HIPAA Hosting vs. Standard Hosting: What’s the Difference?
A hard fact of the Internet is that you need machines to be part of it – either on your own or as a service. If you are in the healthcare field and don’t want to set up servers for your HIPAA-compliant website hosting or other services in your own data center, you need HIPAA web hosting.
All hosting is not created equal. Because there is a disparity between security and other checks and balances from one system to another, standards were created to guide oversight of infrastructure and maintain proper protection of patient data. Those standards were developed by the US Health and Human Services Department (HHS), as directed by the Health Insurance Portability and Accountability Act of 1996 (HIPAA). Hence, beyond simple web hosting, anyone who is aiming to secure healthcare records in a healthcare hosting environment needs HIPAA-compliant hosting, sometimes called simply HIPAA hosting.
“HIPAA recognizes all health care providers and their business associates as covered entities (CEs) and makes them responsible to safeguard the privacy and security of identifying information.” “Some CEs, particularly smaller sized CEs, don’t have the resources necessary to implement a system to handle and safeguard health data on their own, so they rely upon the services of HIPAA hosting.”
Jacco Blankenspoor of HIPAA HQ[i]
Any hosting provider can offer HIPAA-compliant hosting services as determined by its own understanding of the healthcare law; in other words, there is no official federal certification process for these business associates. The vetting of the quality of HIPAA hosting infrastructure that backs any hosted services must be determined by the healthcare-covered entities that use their services – that is to say, healthcare organizations are responsible for verifying the HIPAA compliance of the hosting services they contract.
The government also doesn’t recognize any third-party certification bodies for HIPAA hosting providers. That allows free competition in developing credibility and proving it through legitimate independent parties. However, it also means it’s your responsibility to know the quality of the certification body and what exactly is included in their HIPAA compliance auditing process.

Responsibilities for Safeguarding Electronic Protected Health Information Are Defined by the HIPAA Final Rule
Given the surrounding lack of standards for what qualifies as “HIPAA-compliant hosting,” there is a positive for covered entities: Business associates (BAs – this includes HIPAA-compliant web hosting providers) are now responsible for data in the same manner as covered entities (healthcare providers, plans, and data clearinghouses) are – after implementation of the Omnibus HIPAA Final Rule (often called just the Final Rule or Omnibus Rule; activated March 26, 2013).
Following passage of the rule, business associates “are liable for PHI uses and disclosures and HIPAA Security Rule compliance.” “Additionally, BAs with their subcontractors, while BAs – not covered entities – are also now responsible for responding to any noncompliant subcontractors.”
Elizabeth Snell of HealthIT Security[ii]
Health and Human Services additionally created a process through which randomly chosen covered entities would be audited for HIPAA compliance, including adherence to the all-important Security, Privacy, and Breach Notification Rules.

What Is HITECH?
HITECH (the Health Information Technology for Economic and Clinical Health Act of 2009) was an effort to keep the transition to digital health data as safe as possible. While HITECH describes how electronic health records can be shared, HIPAA assigns responsibility for data security to any organization or individual that accesses and uses electronic protected health information (ePHI).
Specific security methods are at your discretion, though, to an extent. “[T]he HHS allows entities to implement their own chosen methods,” said Blankenspoor. “However, there are best practices used in the industry that the HHS would expect entities to make use of, or show that they are able to implement a comparable or better system.”

What Are Examples of Covered Entities and Business Associates?
The term “covered entity” specifically includes all healthcare providers, plans, and data clearinghouses operating in the United States. Like their business associates – contracted through a business associate agreement, per HIPAA – covered entities have to independently meet all HIPAA compliance rules.
The business associate agreement outlines responsibilities for protecting patient data between the covered entity and the business associate, and a business associate agreement is a must when choosing a HIPAA hosting provider.
Essentially, the covered entities are healthcare organizations and agencies that are more directly healthcare-related – that is, their core operations require the handling of protected health information (PHI). What is a business associate? HIPAA-compliant hosting services providers are one example of a business associate under HIPAA. Others requiring a business associate agreement include medical billing services and shredding companies.

HIPAA Violations Can Result in Jail Time
Like anything in business, a company might look at HIPAA and decide they are not going to invest in meeting its guidelines. Within the law, that refusal to comply is called willful neglect. Fines for this violation are $10,000-$50,000. The total a single company can be fined per year is $1.5 million. It’s also possible to be sentenced to jail time for willful neglect of HIPAA that results in sensitive data being exposed.
Neglect isn’t always considered willful. It is sometimes categorized as a reasonable cause. In these situations, 500 or more individual pieces of medical data have become exposed – resulting in $100-$50,000 fines for each violation. Note that these types of violations are never accompanied by jail time.

Top 11 HIPAA Fines by Settlement 2014-2024
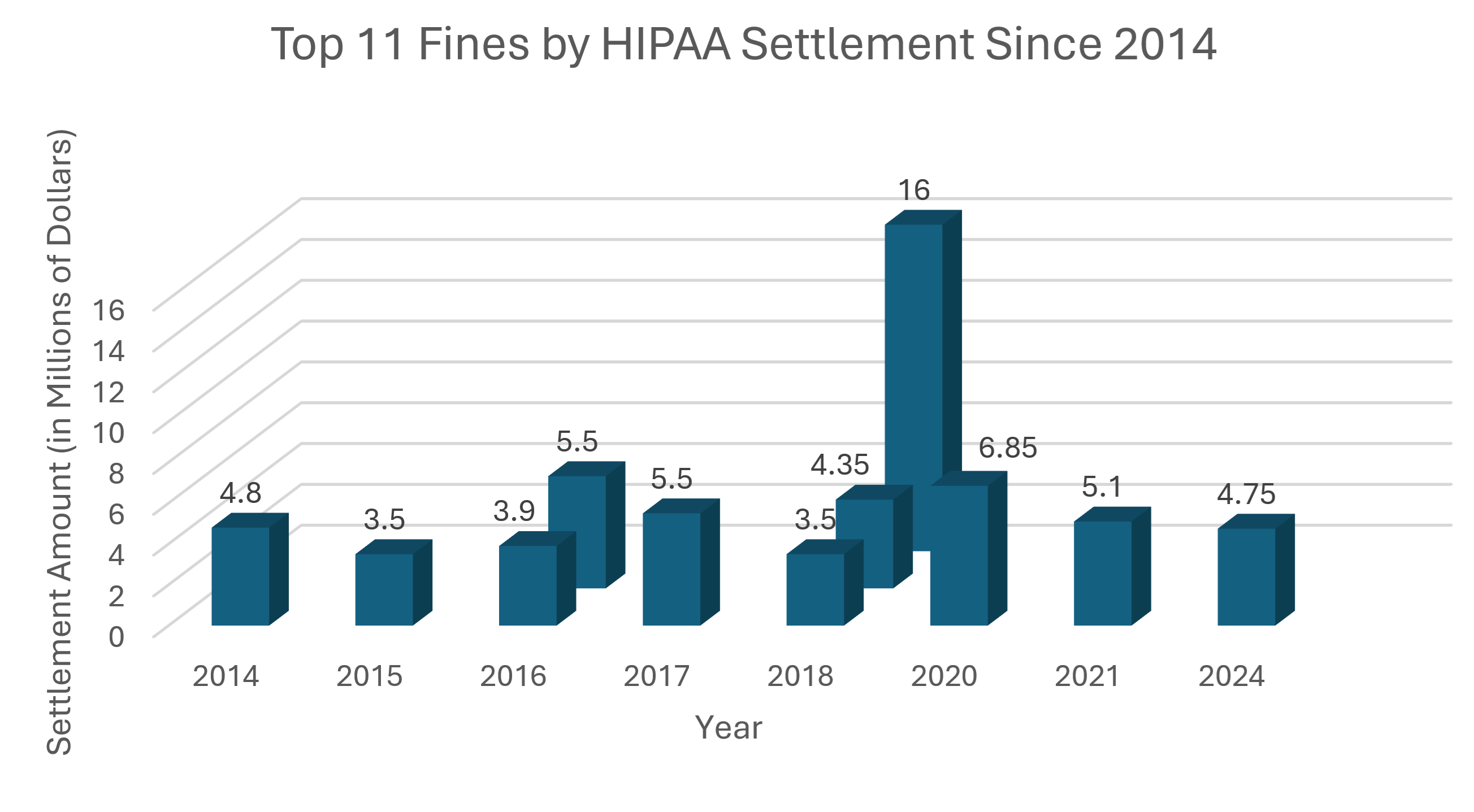
Sources: Compliancy Group and the HIPAA Journal.
Note that 6 of the 11 largest HIPAA fines occurred in 2018, 2020, 2021, or 2024 with the largest HIPAA fine yet in 2018: a $16,000,000 fine against Anthem for a massive HIPAA data breach.

The HHS Audit Program
The random audits began with a pilot program that included 113 companies and other organizations. This pilot process allowed Health and Human Services to better understand best practices both for compliance and for non-compliance (i.e. how they should respond to violations).
“[Atlantic.Net’s] financial strength and proven track record are something we view with great confidence.”
Joseph Nompleggi, Vice President, Complete Healthcare Solutions

What Is the HIPAA Security Rule?
In a nutshell, the Privacy Rule safeguards electronic health records. The Security Rule, however, is the especially pertinent one to HIPAA hosting because it sets more specific expectations for health data storage and transmission – i.e., the realm of ePHI (electronic Protected Health Information).
The HIPAA Security Rule is sectioned into Administrative Safeguards, Physical Safeguards, and Technological Safeguards. It has gradually become more prominent because of adaptations in the digital world and the expansion of different, newer technological methods.
“The same standards for the privacy and confidentiality of healthcare data apply to PHI and ePHI,” advised Blankenspoor, “but the processes used to keep data private are much more complex and technical for electronic data files and ePHI than they are for paper files.”
“The Health Insurance Portability and Accountability Act of 1996 (HIPAA) required the Secretary of the U.S. Department of Health and Human Services (HHS) to develop regulations protecting the privacy and security of certain health information.1 To fulfill this requirement, HHS published what are commonly known as the HIPAA Privacy Rule and the HIPAA Security Rule. The Privacy Rule, or Standards for Privacy of Individually Identifiable Health Information, establishes national standards for the protection of certain health information. The Security Standards for the Protection of Electronic Protected Health Information (the Security Rule) establish a national set of security standards for protecting certain health information that is held or transferred in electronic form. The Security Rule operationalizes the protections contained in the Privacy Rule by addressing the technical and non-technical safeguards that organizations called “covered entities” must put in place to secure individuals’ “electronic protected health information” (e-PHI). Within HHS, the Office for Civil Rights (OCR) has responsibility for enforcing the Privacy and Security Rules with voluntary compliance activities and civil money penalties.”[iii]
[i] HIPAA compliant hosting explained
[ii] http://healthitsecurity.com
[iii] laws regulations
This article was updated with the latest content on April 3, 2025.