Table of Contents
Let’s face it, businesses now have more opportunities thanks to the development of digital technologies and the growing popularity of online transactions. But these developments also bring with them a number of difficulties, particularly when defending private financial data and stopping questionable activity in transactions.
Whether you are a regular customer or a business owner, you must safeguard your financial information, so it is important to recognize warning signs and fraudulent activity! Thankfully, even though it may sound frightening, there are a few techniques you can pick up on to identify those warning signs before any harm is done quickly.
Remember that knowledge is power, and you give yourself and your company a significant advantage when you study and conduct research, particularly in these delicate business areas.
So, you must be wondering: What is cloud-based technology? Let’s get into it.
Photo by Philipp Katzenberger on Unsplash
Cloud-based technology navigation
The use of the internet to deliver computing services has changed dramatically with the advent of cloud-based technology, or cloud computing. Instead of depending on local computers or hardware, it enables users to access applications, storage, and resources via a network or remote servers.
This novel approach has had a profound effect on a wide range of industries, most notably banking and finance. Recently, several financial institutions have transitioned their transaction monitoring processes from traditional on-premise systems to cloud-based solutions.
The primary drivers behind this shift have been the need for enhanced flexibility, quick adjustments to evolving regulatory demands, and the desire to take advantage of the cutting-edge features provided by cloud computing.
Thanks to cloud-based solutions, financial institutions can respond to changing market conditions faster, cut costs associated with operations, and become more competitive overall in the ever-changing financial industry.
Red flags and anomalies in transactions
Recognizing any odd or abnormal behavior that might point to possible fraud or illegitimate activity is necessary to identify red flags and suspicious activities in transactions.
It is critical to recognize these warning signs because they can help businesses avoid lawsuits, reputational damage, and financial losses. It is necessary to become acquainted with typical instances that fall into this category in order to obtain an understanding of how red flags in transactions are addressed by cloud-based technology:
- Transactions that are unusually large in comparison to the usual patterns of activity for a particular account or company may give rise to suspicions about money laundering or other illegal activity.
- Suspicious login attempts from unknown IP addresses or devices or at odd hours may indicate unauthorized access.
- Small, frequent and quick transactions might also be signs of fraud.
- Customer complaints may indicate possible problems, like unauthorized account access or charges that are not authorized.
- When a single person or organization uses multiple accounts for similar transactions, this could indicate fraud in money laundering.
- Phishing emails, suspicious emails, or requests for private information may be signs of impending fraud.
- Deals from high-risk countries or regions might be flagged, especially if the company has not done any business there before.
- Activities within the organization, such as unauthorized access or unusual transactions by employees, can also be considered red flags.
However, these warning signs are easily manageable, particularly when we move on to the next section. Investigating the underlying accountability that goes along with the aforementioned inconveniences is necessary. Two critical areas of focus in this ongoing investigation are data security and fraud prevention.
Maintaining the integrity of interactions is not impossible to achieve when it comes to cloud-based technology. These include secure data storage, multi-factor authentication, and encryption, real-time monitoring, advanced machine learning algorithms, and deriving insights from past data analysis.
Real-time monitoring in the Cloud
One of the primary methods of preventing fraud is real-time monitoring, which is a crucial advantage you can invest in. Cloud-based solutions transform the process, unlike conventional methods, where data processing and analysis may experience major time delays.
Combining the best transaction monitoring tool with cutting-edge technologies like artificial intelligence (AI) and machine learning (ML) makes it possible to gain immediate insight into transactions as they happen.
Real-time monitoring identifies anomalies in user behavior or deviations from typical transaction patterns quickly by utilizing complex pattern recognition algorithms.
With the help of machine learning, the system becomes more adaptive and can eventually identify changing fraudulent patterns. Automated responses can halt suspicious transactions, and predefined thresholds cause instant alerts for possible fraud.
An additional degree of security is added by integration with authentication mechanisms. Businesses that receive immediate alerts are guaranteed prompt action, allowing for prompt confirmation or remedial actions in response to suspected fraudulent activity.
Stated differently, the ability of real-time monitoring to promptly detect transaction anomalies is the most important feature. This is noteworthy because it enables businesses to react quickly to possibly deceitful activity and stop it before it causes serious problems.
Machine learning secret in cloud-based transaction security
In real-time, machine learning algorithms closely examine transaction patterns, acting as digital sentinels. They quickly identify and draw attention to any divergences from accepted standards with a hint of artificial intelligence, serving as an alert early-warning system.
By observing your online activity, machine learning algorithms pick up on anomalous patterns. Examining your regular transactions and activities builds a digital fingerprint of what is deemed normal. They analyze vast amounts of data to find patterns and relationships by using advanced mathematical models and statistical techniques.
The algorithms quickly identify any deviations from this established norm.
Because the algorithms are developed to be sensitive to these variations, they function as a kind of alert buddy, sounding an alarm whenever they notice a transaction or activity that deviates from the patterns they have inferred from your typical behavior.
Over time, these algorithms’ capacity to recognize abnormalities improves due to ongoing learning and adaptation.
Analyzing historical data for suspicious patterns
Cloud-based systems use complex algorithms and data processing methods to identify historical data. These algorithms are made to sort through large amounts of transactional history data and identify trends, abnormalities, and patterns.
In cloud-based systems, Tableau, Power BI, and Google Analytics are examples of advanced analytics platforms useful for visual exploration when analyzing historical data. Big data frameworks like Apache Spark and database systems like MySQL effectively manage enormous datasets.
Relevant data can be extracted using query languages like SQL, and storage can be centralized using data warehousing solutions like Amazon Redshift. By automating the identification of anomalies, specialized pattern recognition software improves the system’s capacity to proactively detect and handle probable fraudulent activity in historical transaction data.
Photo by Ed Hardie on Unsplash
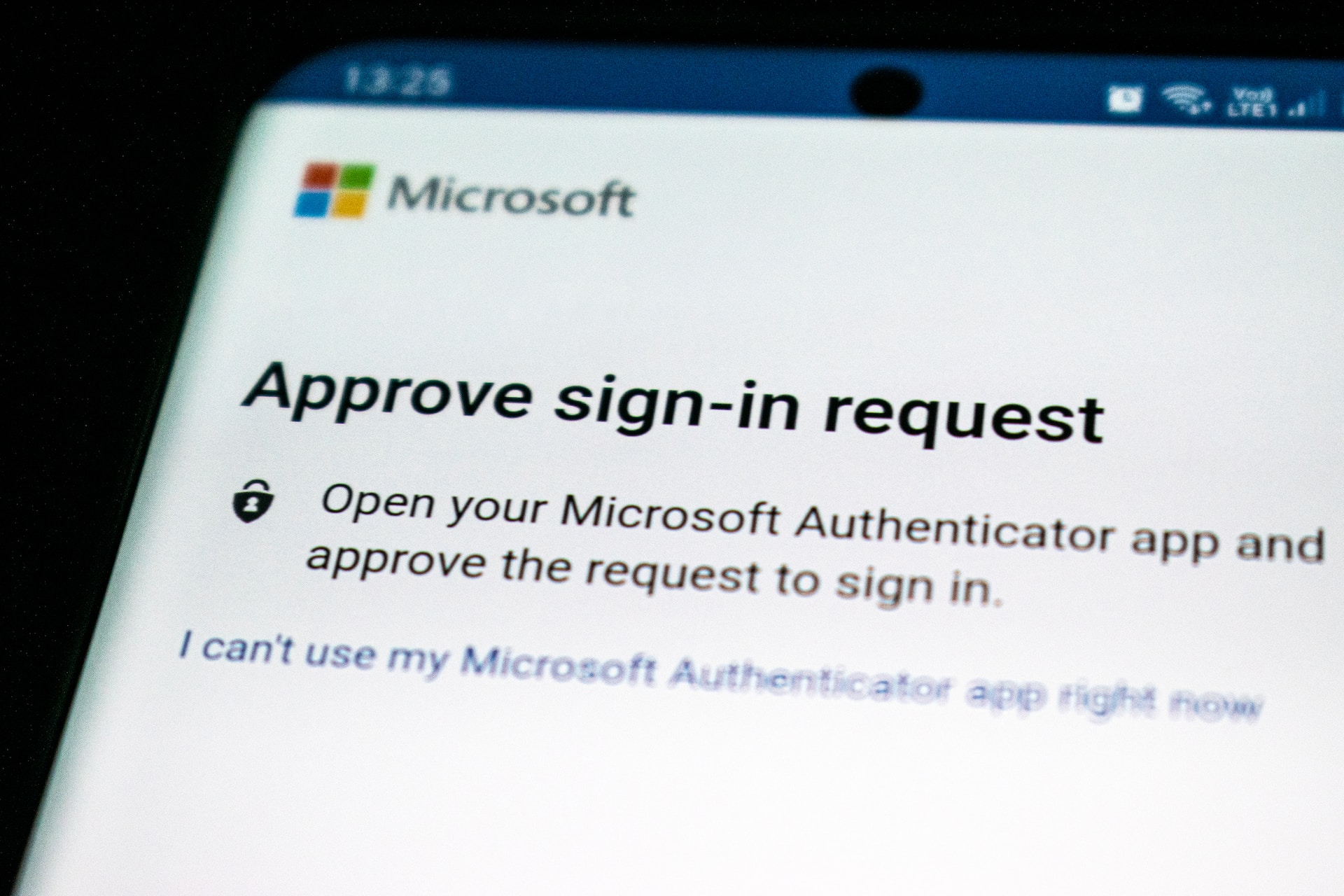
Implementation of Multi-Factor Authentication
Multi-factor authentication (MFA) is implemented by adding additional layers of security on top of the conventional username and password setup.
Cloud platforms require users to experience additional verification steps, such as entering a one-time code sent to their mobile device or using biometric identification such as fingerprints.
Multi-factor authentication (MFA) often incorporates several factors, such as something you own (a physical device, such as a smart card, security token, or mobile device that generates or receives a one-time code), something you know (a password or PIN), or both.
Biometric data such as fingerprints, face recognition, and retinal scans are examples of what constitutes your unique identity. In addition to actions such as mouse clicks or keystroke patterns, other components—like geolocation data confirming the user’s location—provide information about where you are.
A stronger authentication procedure is achieved by combining these components and adding more factors, which lowers the possibility of unwanted access and possible security breaches.
Encryption and secure data storage
Resilient encryption and data storage procedures are the cornerstones of data security in cloud environments. Like a secret code, encryption converts important data into an unintelligible format that can only be interpreted with the right decryption key.
Cloud platforms use encryption to protect data during transmission and while stored in databases. Access controls, and authentication procedures are also implemented as part of secure data storage practices to prevent unwanted access.
Encryption is a security measure used in cloud computing to protect sensitive data by converting it into an unreadable format. Cloud databases with access controls are used to store this encrypted data, which is safely transferred via protocols like HTTPS. Thanks to effective key management, only authorized users with the right credentials can decrypt the data.
Regular audits and monitoring of access logs and encrypted data are necessary to detect and prevent potential cyberattacks to maintain the overall security posture.
This strengthened protective layer preserves the confidentiality and integrity of sensitive data stored in the cloud, which guarantees that even in the event of unauthorized access, the encrypted data remains unintelligible.
Secure data storage combined with encryption creates a strong barrier against potential breaches and illegal intrusions.
Photo by Philipp Katzenberger on Unsplash
Cloud-based technology means automation and scalability
Using cloud-based technology is a smart move for companies of all kinds in this fast and technologically advanced era. Beyond its affordability and usefulness, this technology has arisen as a shining example of innovation, enabling companies to take proactive measures against fraudulent activity.
In addition to improving security, it is about guiding companies and organizations toward a flexible and expanding future, ensuring no one falls behind the curve, and establishing a strong and competitive presence in the market.
As a result, let us embrace the cloud rather than just adopt it since it will become essential to achieving the ever-changing business agenda.